Category: CyberSecurityNews
A sophisticated new malware strain targeting Linux environments has emerged, demonstrating advanced evasion capabilities that challenge traditional endpoint detection and…
The cybersecurity landscape continues to witness sophisticated threat actors developing increasingly complex attack methodologies to infiltrate organizational networks and steal…
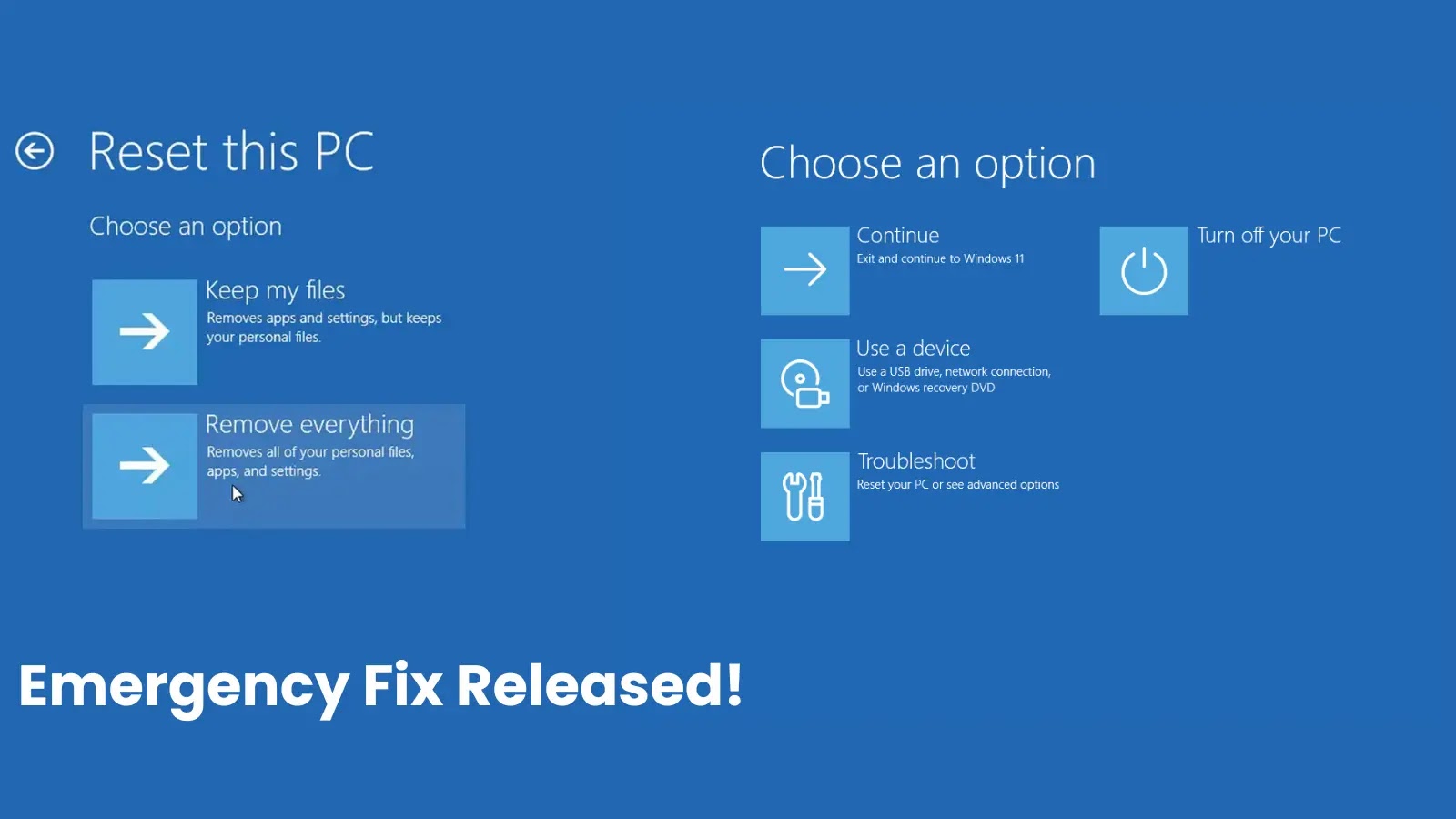
Microsoft has issued critical out-of-band updates on August 19, 2025, to address a significant issue affecting Windows reset and recovery…
A sophisticated campaign uncovered where adversaries are exploiting CVE-2023-46604, a critical remote code execution vulnerability in Apache ActiveMQ, to compromise…
A Chrome VPN extension with over 100,000 installations and verified badge status has been discovered operating as sophisticated spyware, continuously…
A sophisticated new Remote Access Trojan named GodRAT has emerged as a significant threat to financial institutions, leveraging deceptive screen…
A sophisticated new Phishing-as-a-Service (PhaaS) framework dubbed “Salty 2FA” has emerged as a significant threat to Microsoft 365 users across…
Google has released an emergency security update for Chrome to address a critical vulnerability that could allow attackers to crash…
Microsoft is in the process of deploying a fix for a service degradation issue affecting Microsoft Teams users globally, which…
Key Takeaways1. ShinyHunters publicly released exploits for critical SAP vulnerabilities.2. Unauthenticated attackers can achieve complete system takeover and remote code…
A sophisticated espionage campaign targeting diplomatic missions in South Korea has exposed the evolving tactics of North Korean state-sponsored hackers….
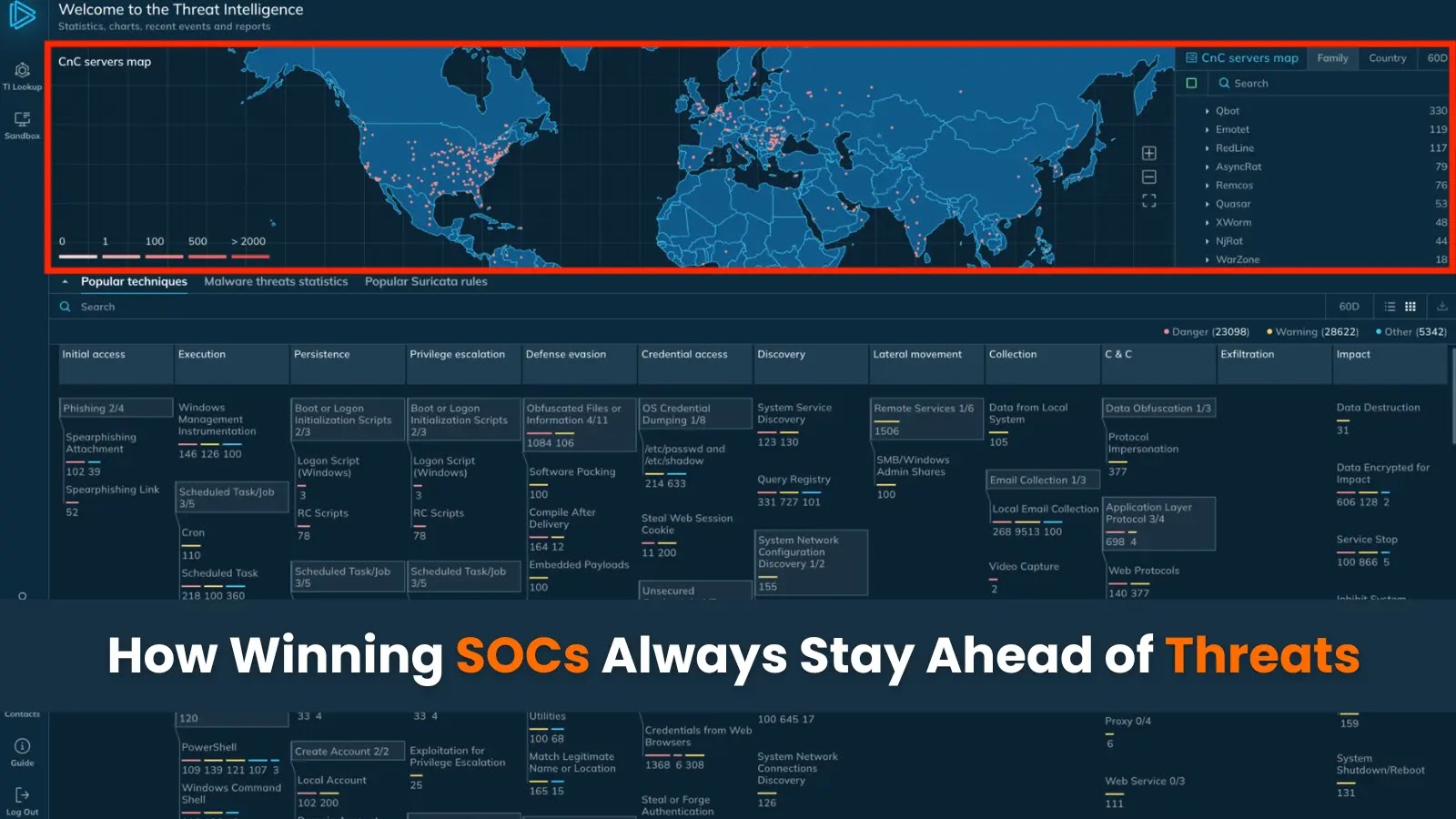
Despite the escalating danger of cybersecurity breaches, high-performing Security Operations Centers are able to maintain their resilience and prevent attacks….