Category: CyberSecurityNews
A sophisticated Chinese threat actor campaign has emerged as one of the most persistent malware distribution operations targeting Chinese-speaking communities…
A sophisticated phishing campaign targeting organizations has emerged, exploiting the trusted reputation of Veeam Software through weaponized WAV audio files…
A critical zero-day flaw in the CrushFTP managed file-transfer platform was confirmed after vendor and threat-intelligence sources confirmed active exploitation…
A sophisticated phishing campaign dubbed “Scanception” has emerged as a significant threat to enterprise security, leveraging QR codes embedded in…
The cybersecurity landscape continues to face significant threats from sophisticated information stealers, with Lumma emerging as one of the most…
The U.S. Cybersecurity and Infrastructure Security Agency (CISA) has added a critical Fortinet FortiWeb vulnerability to its Known Exploited Vulnerabilities…
Google has filed a lawsuit in New York federal court against the operators of the BadBox 2.0 botnet, marking a…
A stealth Monero-mining campaign has quietly compromised more than 3,500 websites by embedding an innocuous-looking JavaScript file called karma.js. The…
Russian premium vodka producer Beluga, owned by NovaBev Group, has fallen victim to a sophisticated ransomware attack that disrupted its…
A buffer overflow vulnerability in Lenovo Protection Driver could allow local attackers with elevated privileges to execute arbitrary code on…
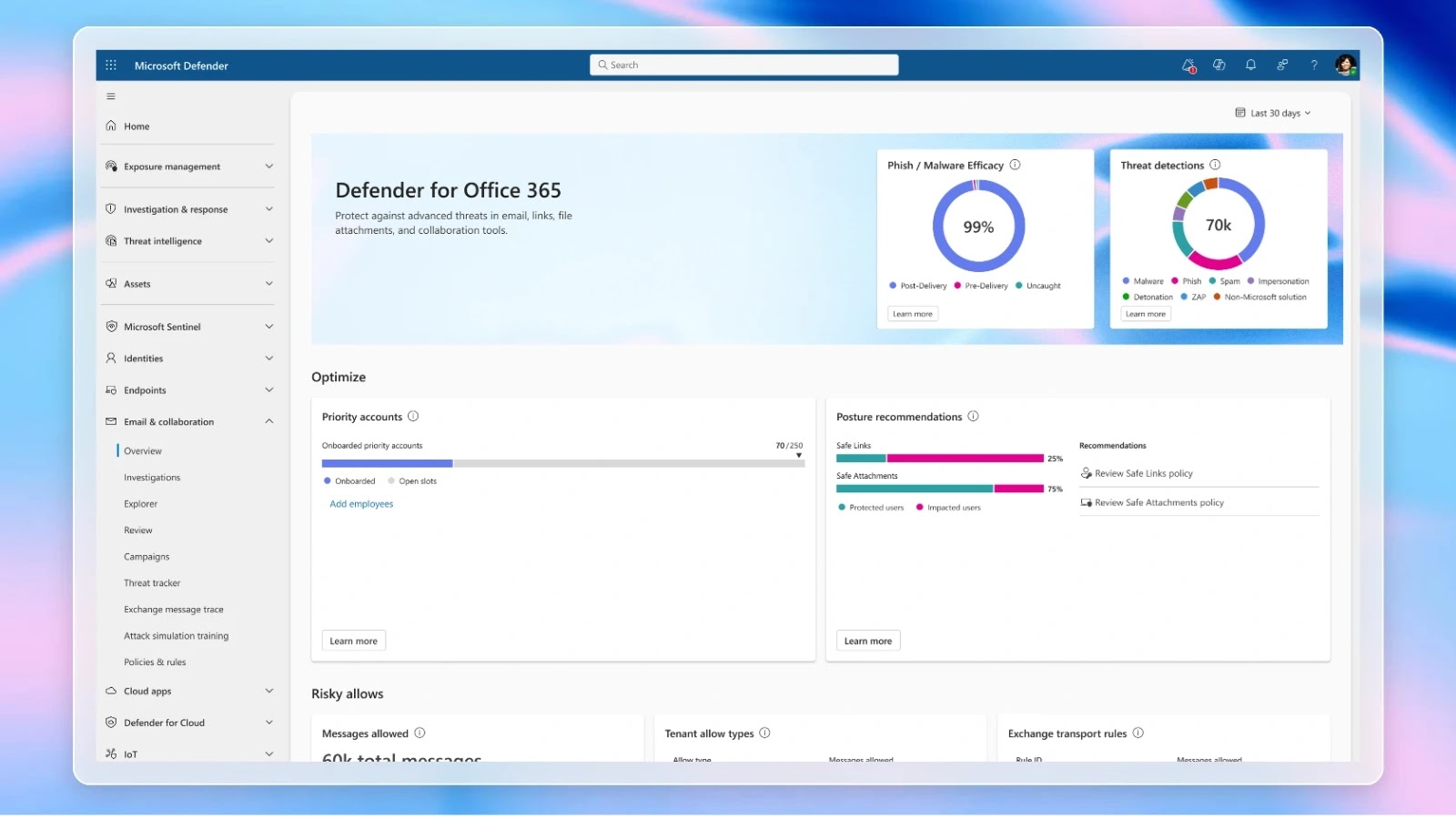
Microsoft today announced the rollout of a revamped customer dashboard in Microsoft Defender for Office 365, designed to deliver unprecedented…
Three critical vulnerabilities in the Sophos Intercept X for Windows product family could allow local attackers to achieve arbitrary code…