Category: CyberSecurityNews
The notorious Russian cyberespionage group Fancy Bear, also known as APT28, has intensified its operations against governments and military entities…
A sophisticated malware campaign targeting Ivanti Connect Secure VPN devices has been actively exploiting critical vulnerabilities CVE-2025-0282 and CVE-2025-22457 since…
A critical security vulnerability affecting multiple Ubiquiti UniFi Access devices could allow attackers to execute malicious commands remotely. The vulnerability,…
A sophisticated Malware-as-a-Service operation has emerged that exploits the trusted GitHub platform to distribute malicious payloads, representing a significant evolution…
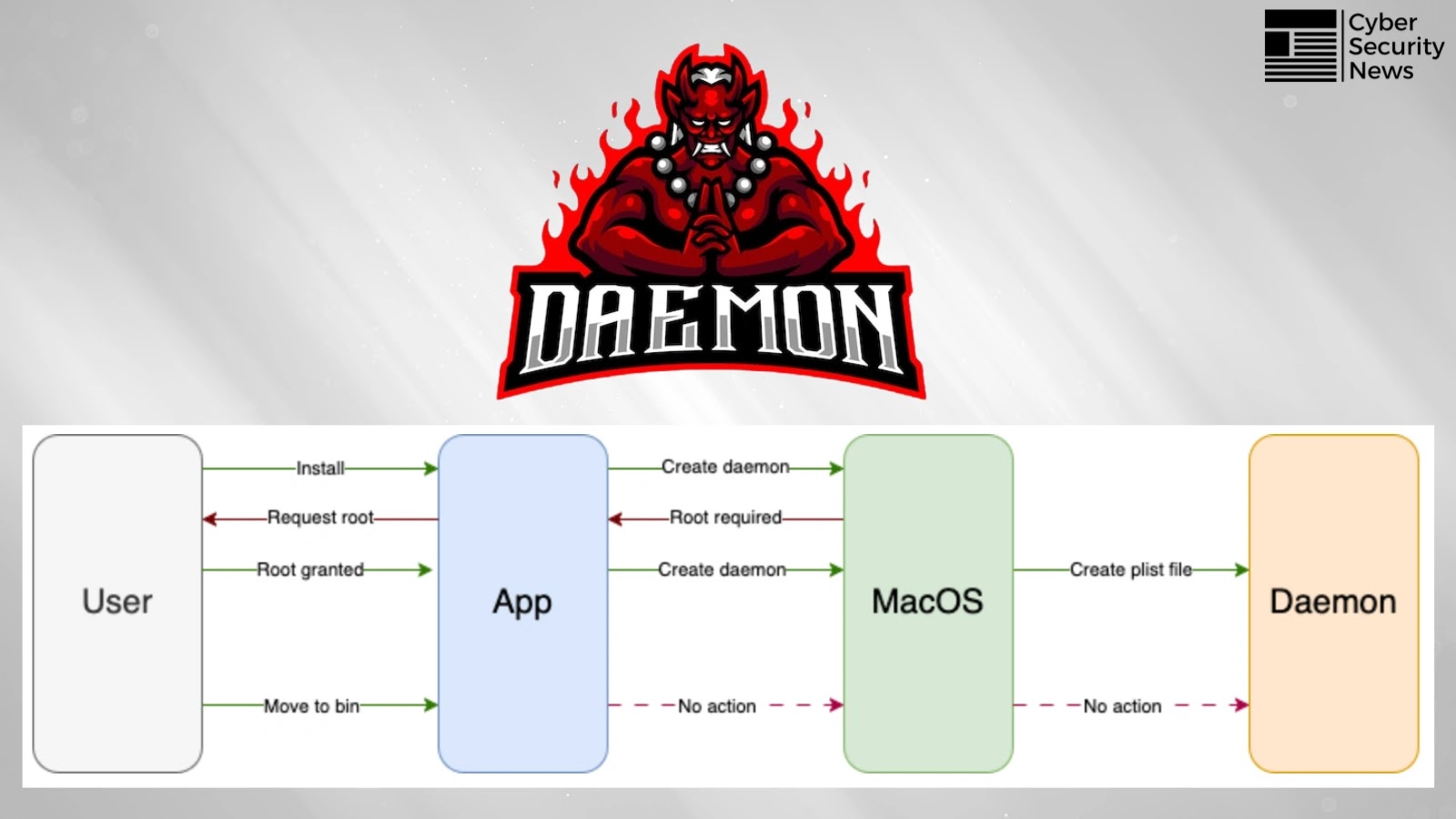
A critical vulnerability in macOS allows attackers to escalate privileges to root access through misconfigured daemon services. The vulnerability, dubbed…
In mid-2025, a new surge of targeted intrusions, attributed to the threat group known variously as Scattered Spider, Octo Tempest,…
CISA issued three significant Industrial Control Systems (ICS) advisories on July 17, 2025, addressing critical vulnerabilities affecting energy monitoring, healthcare…
A critical security vulnerability in TeleMessageTM SGNL, an enterprise messaging system modeled after Signal, has been actively exploited by cybercriminals…
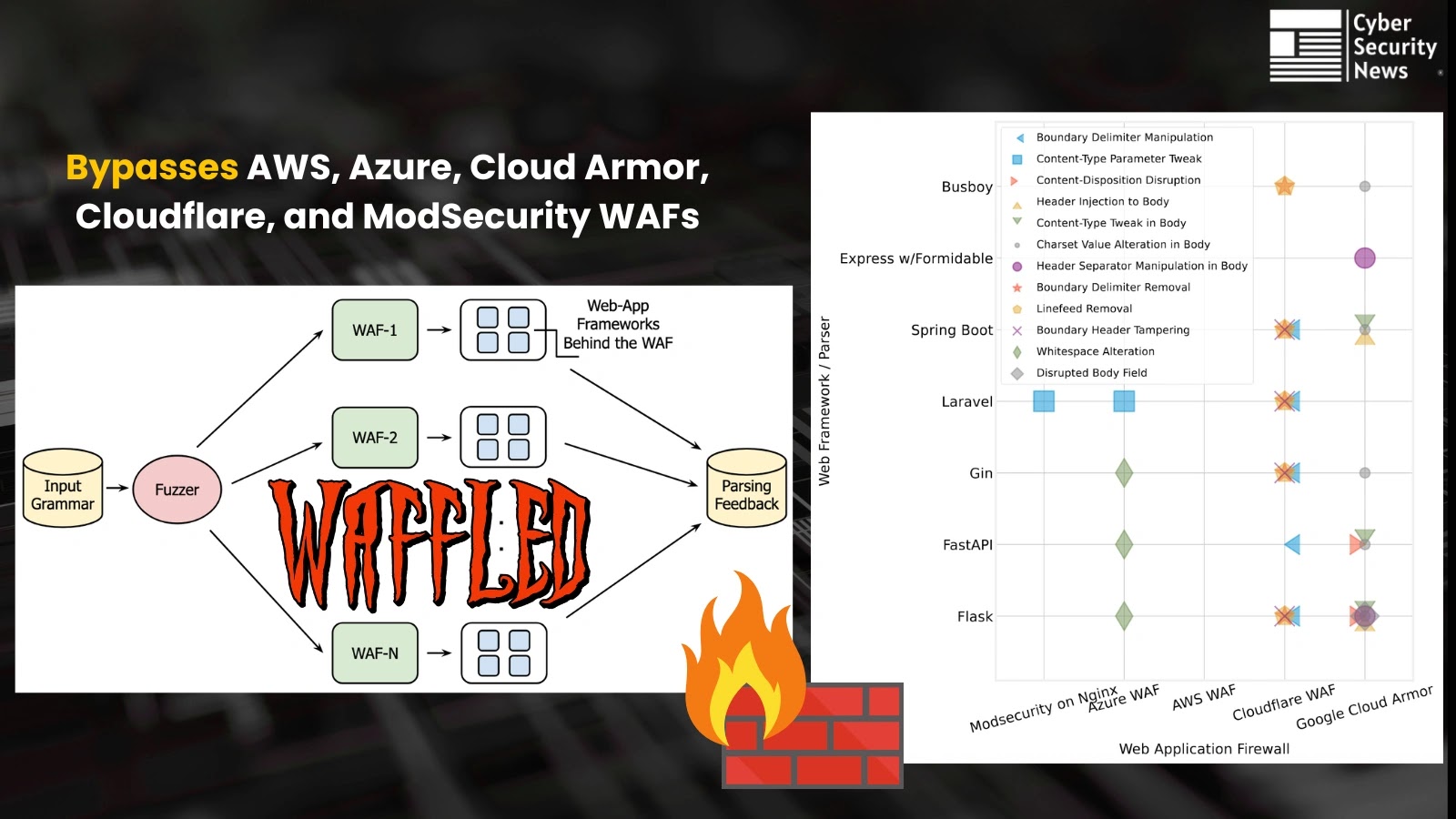
WAFFLED is a recently disclosed technique that evades leading Web Application Firewalls (WAFs) by targeting subtle parsing inconsistencies rather than…
Two critical vulnerabilities in the BIND 9 DNS resolver software are affecting organizations worldwide, with potential cache poisoning and denial-of-service…
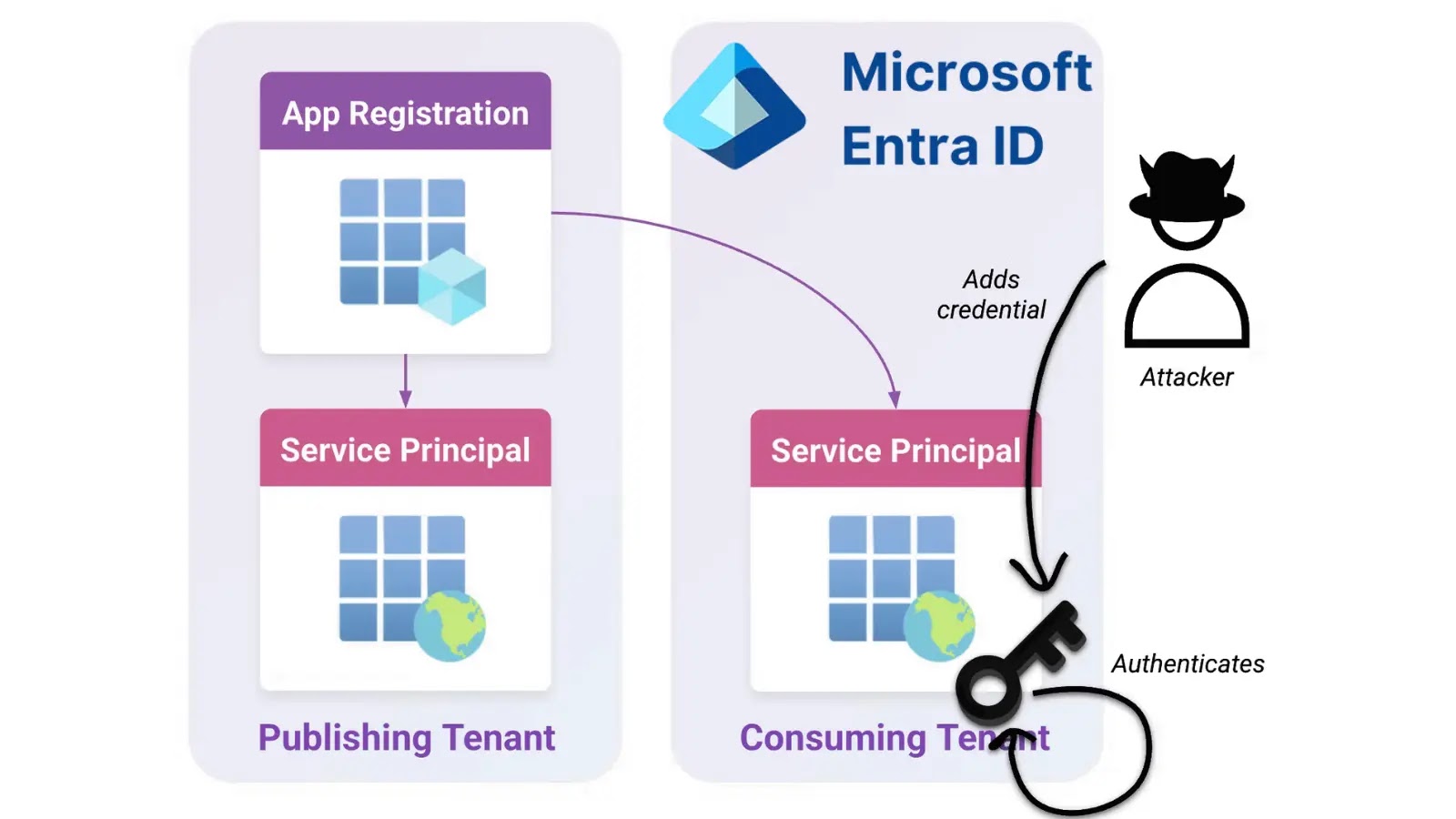
A critical vulnerability in Microsoft Entra ID allows attackers to escalate privileges to the Global Administrator role through the exploitation…
Last week, Ukraine’s Main Intelligence Directorate (GUR) orchestrated a sophisticated cyberattack against Gaskar Integration, a leading Russian drone manufacturer. The…