Category: CyberSecurityNews
A sophisticated Chinese state-sponsored cyber espionage campaign has emerged targeting Taiwan’s critical semiconductor industry, employing weaponized Cobalt Strike beacons and…
A sophisticated new attack vector where malicious actors are hiding malware inside DNS records, exploiting a critical blind spot in…
The global hacktivist landscape has undergone a dramatic transformation since 2022, evolving from primarily ideologically motivated actors into a complex…
The H2Miner botnet, first observed in late 2019, has resurfaced with an expanded arsenal that blurs the line between cryptojacking…
Researchers have uncovered critical security vulnerabilities affecting millions of computer servers and routers worldwide, stemming from the insecure implementation of…
Emerging in mid-2023 as an apparent successor to Meiya Pico’s notorious MFSocket, the newly identified Android application Massistant has begun…
An Armenian national has been extradited from Ukraine to the United States to face federal charges for his alleged involvement…
A sophisticated espionage campaign targeting multiple Asian jurisdictions has emerged, utilizing weaponized shortcut files and deceptive social engineering techniques to…
Co-op has confirmed that all 6.5 million members of the UK retail cooperative had their personal data compromised during a…
NVIDIA has released critical security updates addressing two significant vulnerabilities in its Container Toolkit and GPU Operator that could allow…
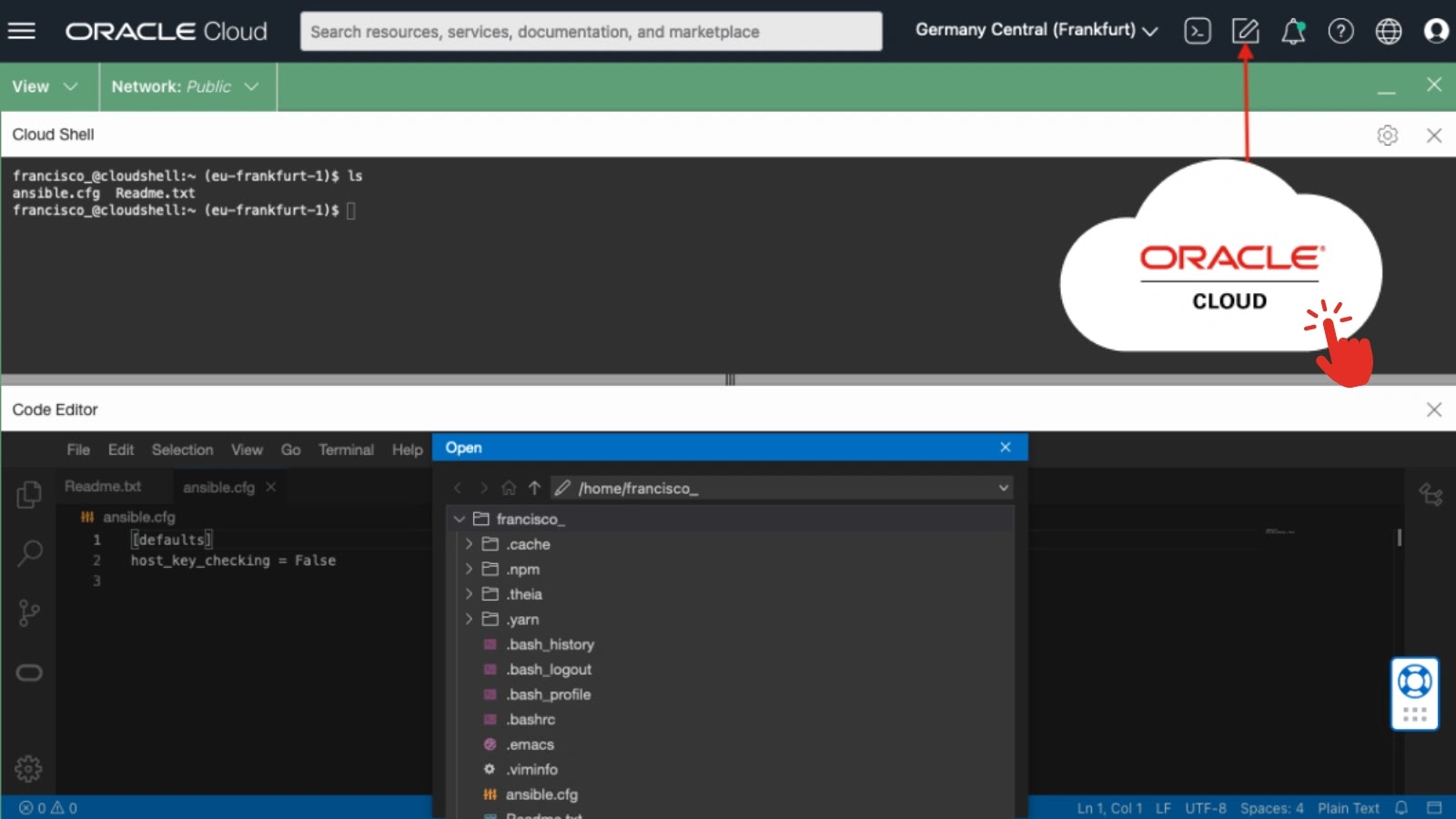
A critical Remote Code Execution (RCE) vulnerability in Oracle Cloud Infrastructure (OCI) Code Editor that allowed attackers to silently hijack…
A highly sophisticated malware campaign targeting Microsoft Exchange servers in government and high-tech organizations across Asia. The malware, dubbed GhostContainer,…