Category: CyberSecurityNews
Summary 1. Redirection controls disable clipboard, drive, USB, and printer access by default to prevent data exfiltration and malware injection….
Microsoft is expanding the number of passkey authentication methods available in Microsoft Entra ID to improve its identity and access…
A new detection method called Jitter-Trap that turns cybercriminals’ own evasion tactics against them, offering new hope in the battle…
A sophisticated new variant of the Masslogger credential stealer has emerged, utilizing VBScript encoded (.VBE) files to deploy a multi-stage…
A critical security vulnerability affecting Cisco Meraki MX and Z Series devices could allow unauthenticated attackers to launch denial of…
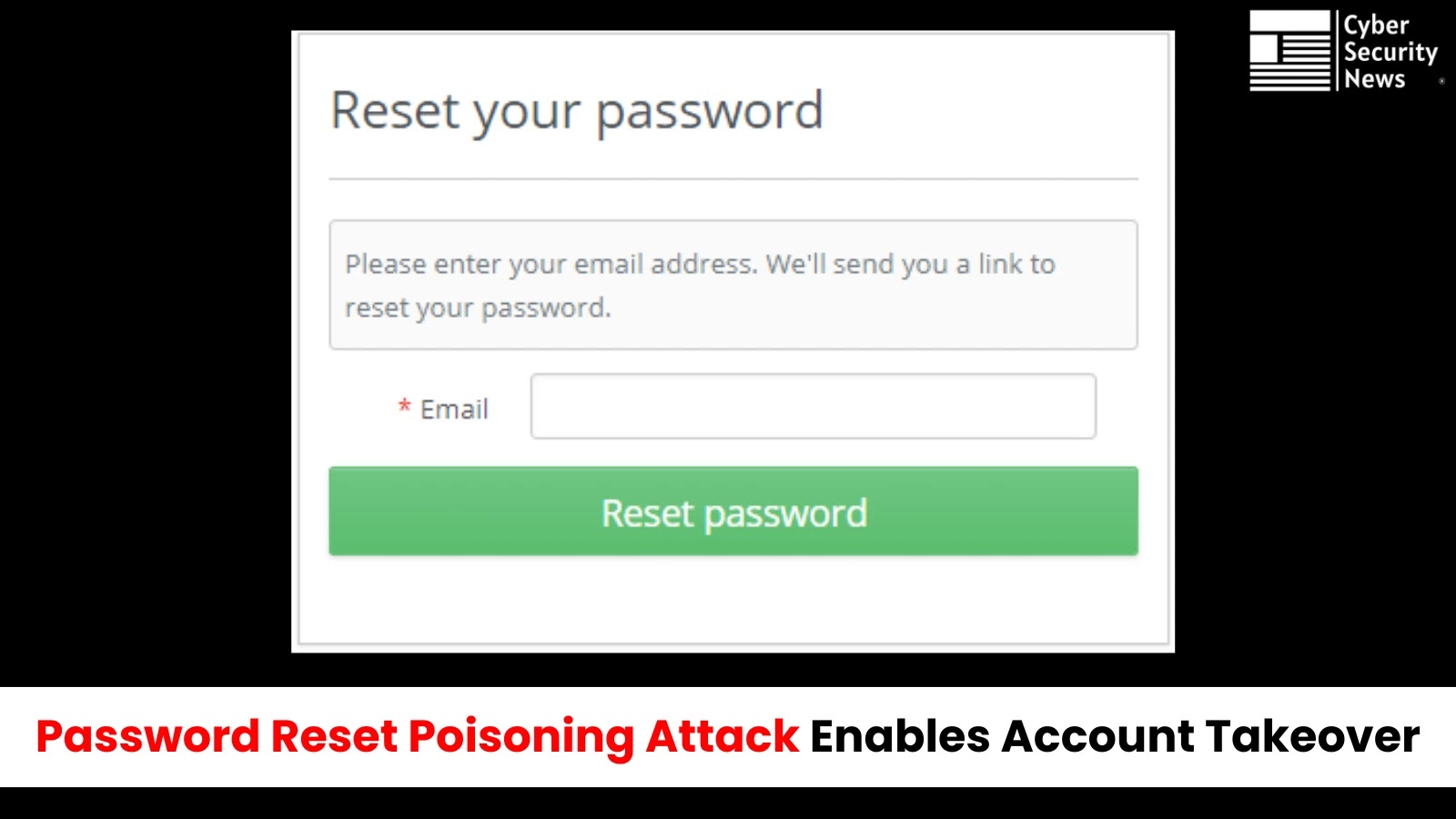
A critical vulnerability in password reset mechanisms has been discovered that allows attackers to completely take over user accounts by…
Cybersecurity professionals are facing a sophisticated new threat as Golden SAML attacks emerge as one of the most dangerous yet…
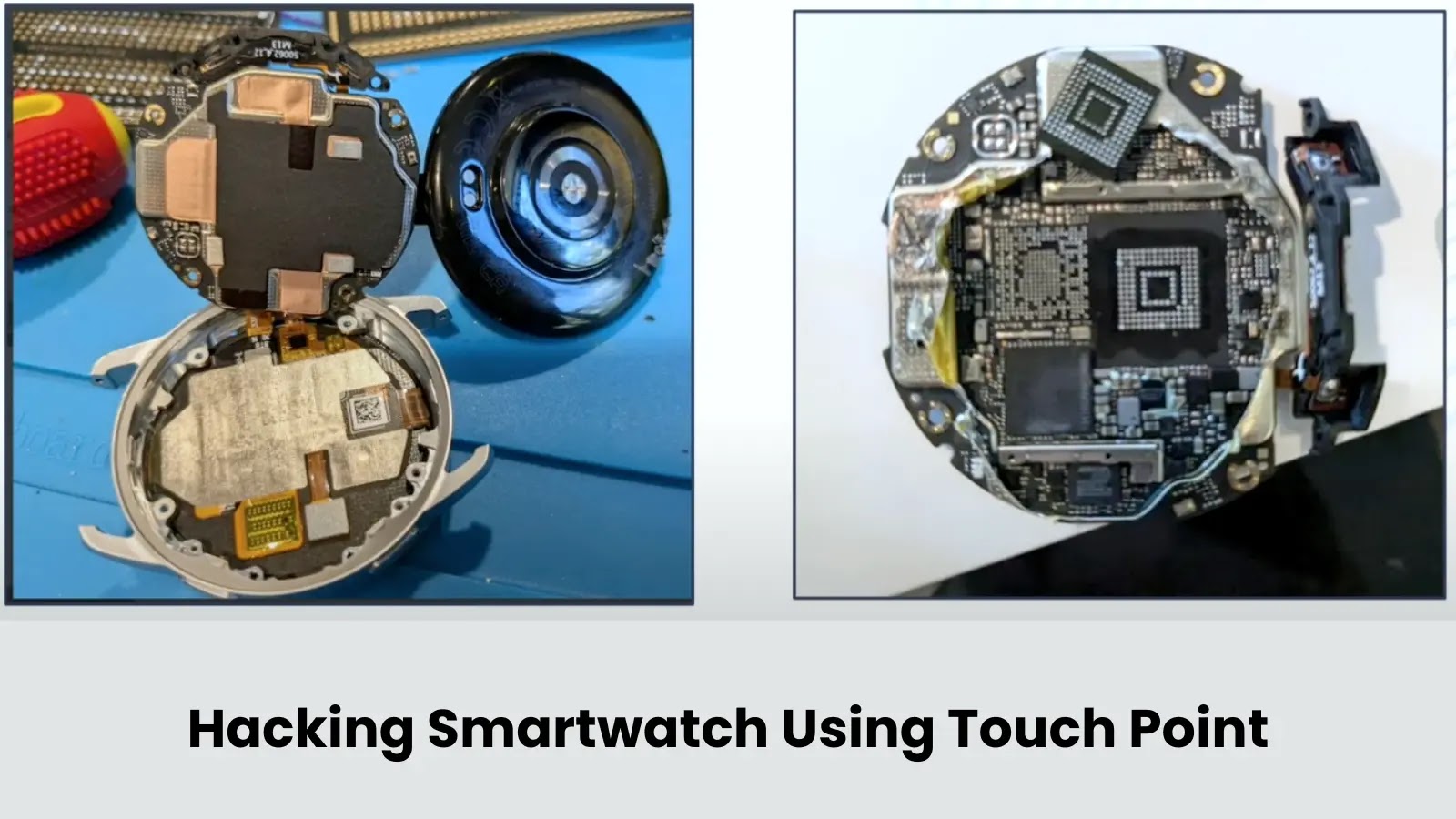
Security researcher Sergei Volokitin has presented findings on hardware vulnerabilities discovered in Xiaomi devices, including the company’s S3 smartwatch, during…
Microsoft has announced a new security capability within its Defender for Office 365 suite aimed at combating the growing threat…
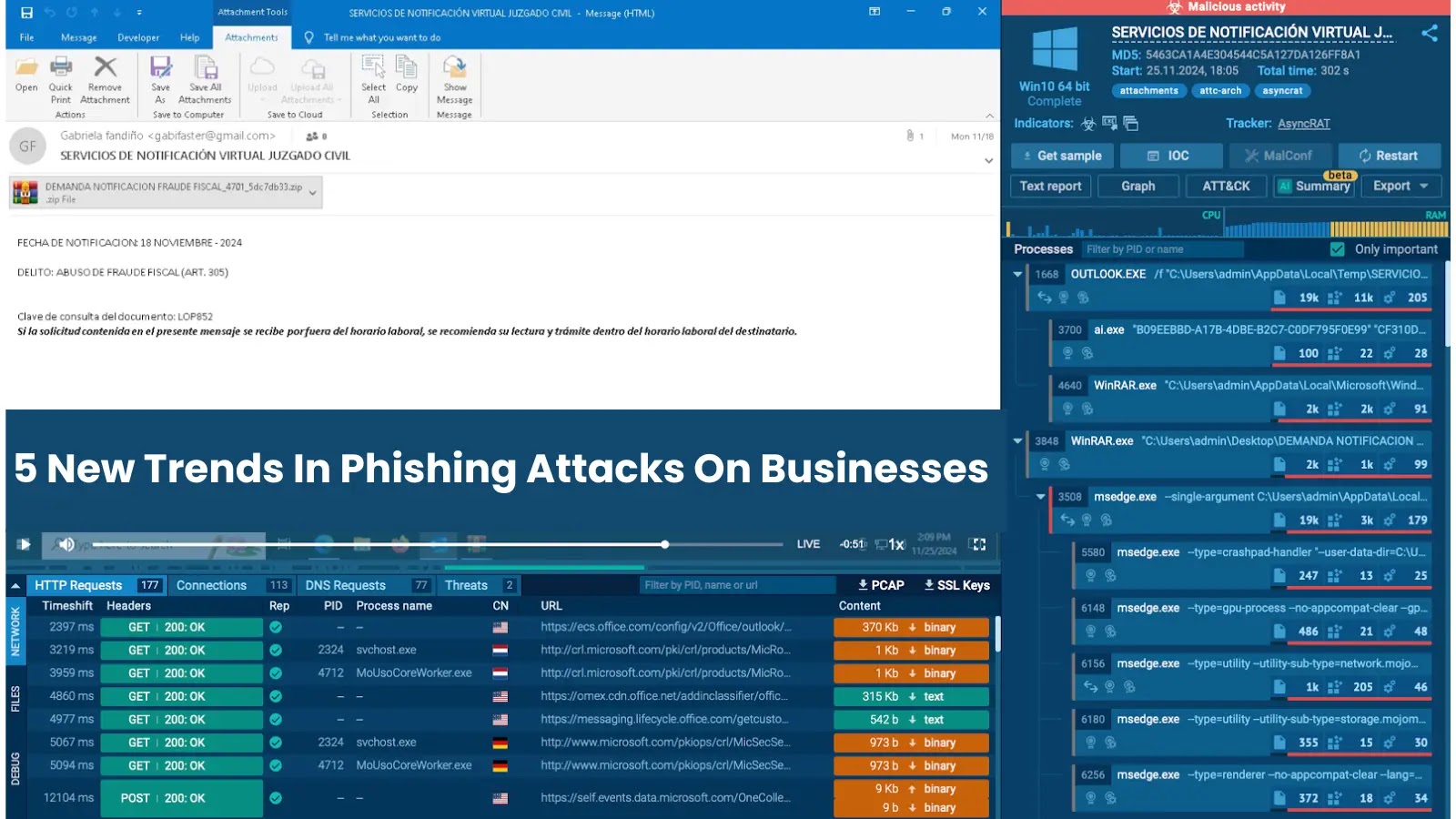
Phishing remains one of the most effective ways attackers infiltrate corporate environments. Today’s phishing campaigns are no longer just poorly…
In a concerning development for mobile payment security, cybersecurity experts have identified a sophisticated new malware strain named “SuperCard” that…
Halo Security’s Attack Surface Management Platform Honored for Exceptional Innovation and Successful Deployment Through The Channel Halo Security today announced that…