Category: CyberSecurityNews
Microsoft 365 users across Asia Pacific, Europe, the Middle East, and Africa are experiencing significant authentication disruptions that are preventing…
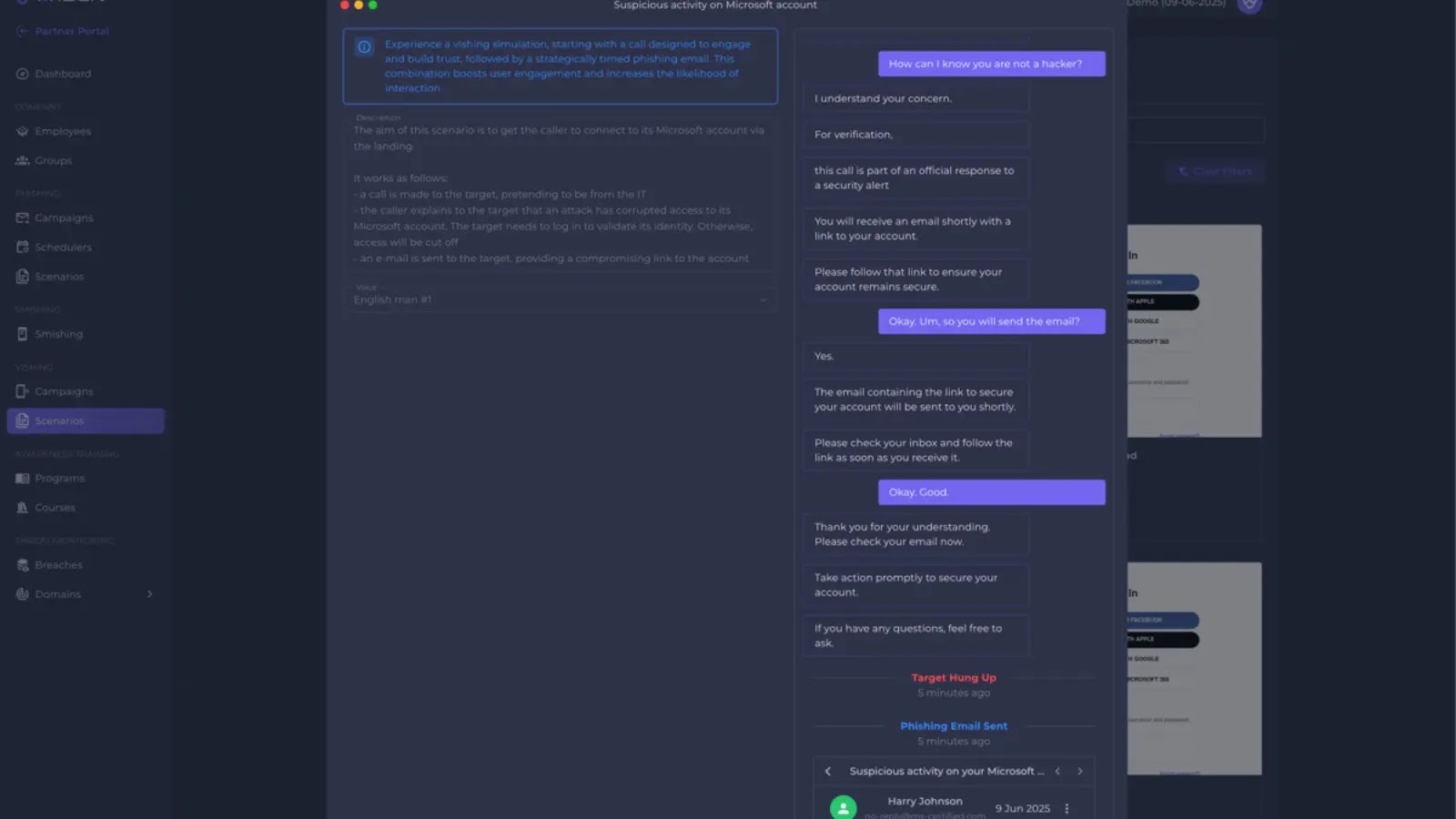
Arsen, the cybersecurity startup known for defending organizations against social engineering threats, has announced the release of its new Vishing Simulation…
The penetration testing community has received a significant upgrade with the release of Kali Linux 2025.2, marking another milestone in…
Despite sustained international pressure, sanctions, and public exposures over the past two years, the sophisticated Predator mobile spyware has demonstrated…
A sophisticated new attack method called “SmartAttack” that can breach supposedly secure air-gapped computer systems using smartwatches as covert data…
Cybersecurity researchers have identified a sophisticated new phishing campaign that exploits GitHub’s OAuth2 device authorization flow to compromise developer accounts…
A significant security vulnerability in HashiCorp Nomad workload orchestrator that allows attackers to escalate privileges by exploiting the Access Control…
The advanced Graphite mercenary spyware, developed by Paragon, targets journalists through a sophisticated zero-click vulnerability in Apple’s iOS. At least…
Cybersecurity researchers have uncovered a sophisticated ransomware campaign targeting utility billing software providers through unpatched vulnerabilities in SimpleHelp Remote Monitoring…
The Fog ransomware group has evolved beyond conventional attack methods, deploying an unprecedented arsenal of legitimate pentesting tools in a…
A critical zero-day vulnerability in WebDAV implementations that enables remote code execution, with proof-of-concept exploit code now publicly available on…
Cybersecurity researchers have uncovered a sophisticated malware campaign that leveraged an advanced JavaScript obfuscation technique to compromise hundreds of legitimate…