Category: CyberSecurityNews
Two of the internet’s most critical infrastructure providers experienced significant service outages yesterday, disrupting millions of users worldwide as both…
Microsoft has resolved a critical bug in Windows Server 2025 that caused Active Directory Domain Controllers to improperly manage network…
A sophisticated cyber threat campaign leveraging malicious unsubscribe links has emerged as a significant security concern, targeting unsuspecting email users…
A critical command injection vulnerability in Palo Alto Networks PAN-OS operating system enables authenticated administrative users to escalate privileges and…
A critical vulnerability in the widely-used OpenPGP.js library has been discovered that allows attackers to forge digital signatures and deceive…
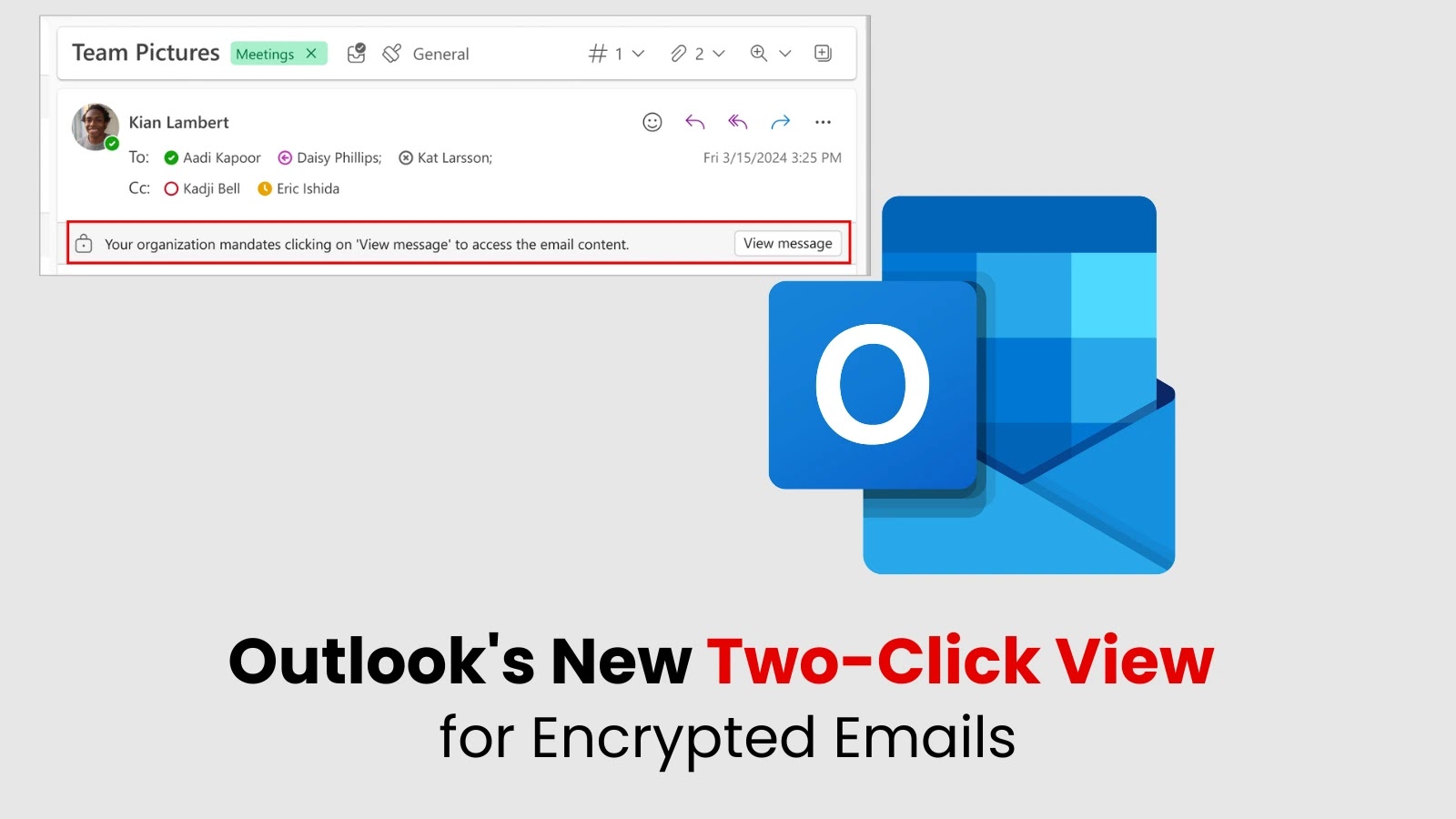
Microsoft is set to launch a significant security enhancement for Outlook users across multiple platforms. Starting April 2025, the company…
Cybersecurity firm Cloudflare has issued a stark warning about the escalating threat landscape facing independent media organizations worldwide, revealing that…
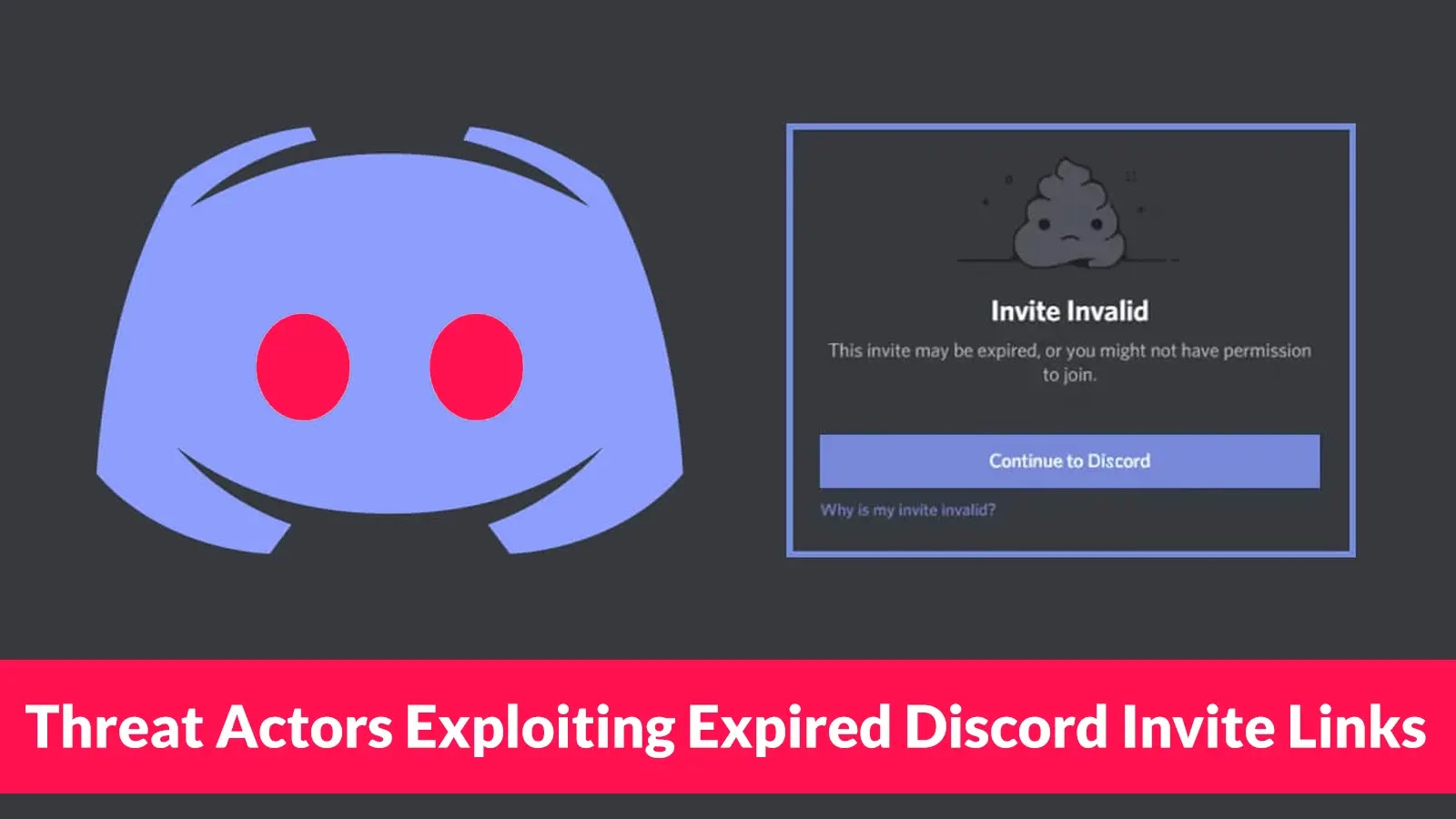
Cybercriminals have discovered a sophisticated new attack vector that exploits a critical flaw in Discord’s invitation system, allowing them to…
The cybersecurity landscape has witnessed the emergence of increasingly sophisticated ransomware operations, with DragonForce standing out as a particularly concerning…
Cybercriminals have begun exploiting the surge in popularity of DeepSeek-R1, one of the most sought-after large language models currently available,…
A series of critical security vulnerabilities across GitLab Community Edition (CE) and Enterprise Edition (EE) platforms that could enable attackers…
A comprehensive security investigation has revealed critical vulnerabilities in OneLogin’s Active Directory (AD) Connector service that exposed authentication credentials and…