Category: CyberSecurityNews
A sophisticated wave of Linux malware campaigns is targeting cloud environments with increasing frequency and complexity, posing significant threats to…
A sophisticated cybercrime campaign has emerged where threat actors are exploiting the trust inherent in professional recruitment processes, transforming routine…
The OWASP Top 10 2021 represents the most critical web application security risks facing organizations today, with significant shifts reflecting…
Secure code review represents a critical security practice that systematically examines software source code to identify and remediate security vulnerabilities…
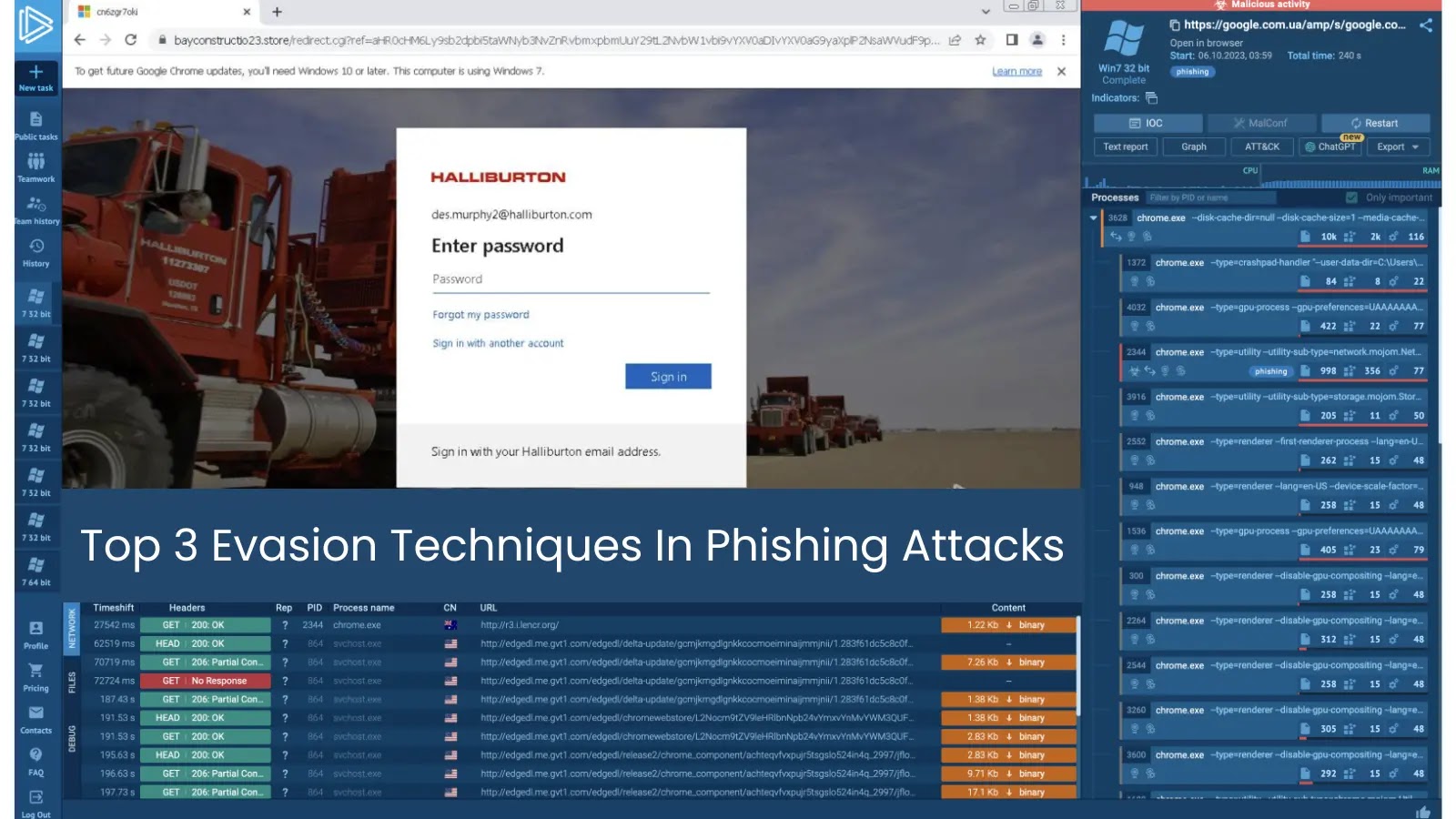
Phishing attacks aren’t what they used to be. Hackers no longer rely on crude misspellings or sketchy email addresses. Instead,…
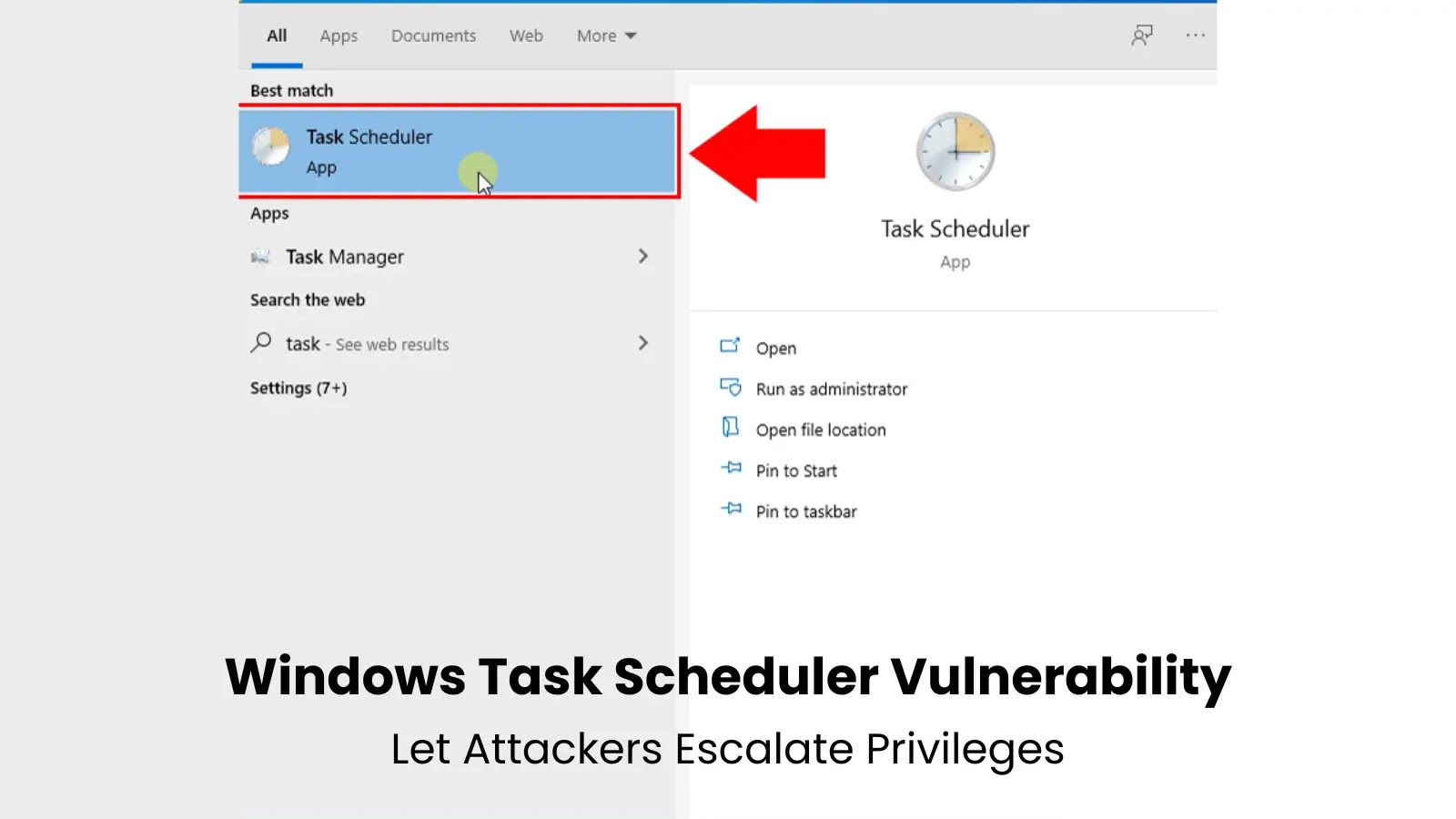
A significant security vulnerability in Windows Task Scheduler could allow attackers to escalate their privileges to SYSTEM level access without…
A high-severity security vulnerability in Hewlett Packard Enterprise (HPE) Aruba Networking Private 5G Core platform that could allow unauthorized actors…
Insider threats represent one of the most challenging cybersecurity risks facing modern organizations, with research indicating that insider data leaks…
Microsoft has announced the introduction of two powerful new data tables to its Defender XDR advanced hunting capabilities, marking a…
Microsoft is set to revolutionize enterprise security monitoring with comprehensive audit logging capabilities for screen sharing and control features in…
Decentralized applications (DApps) have revolutionized blockchain technology by enabling trustless, transparent operations across various industries. However, with over $6 billion…
Microsoft has rolled out the June 2025 Patch Tuesday update for Windows 11, version 24H2, with the release of KB5060842…