Category: CyberSecurityNews
India’s Central Bureau of Investigation successfully dismantled a sophisticated transnational cybercriminal network that impersonated Microsoft technical support services, targeting vulnerable…
Fortinet has released security updates addressing multiple vulnerabilities across its product portfolio, including FortiOS, FortiAnalyzer, FortiProxy, and FortiWeb systems. The…
Microsoft has released its monthly Patch Tuesday updates, addressing a total of 66 vulnerabilities in its product suite. This release…
Fortinet has disclosed a new security vulnerability affecting its FortiOS SSL-VPN web-mode that allows authenticated users to gain unauthorized access…
Modern phishing attacks have evolved far beyond simple deceptive emails, now incorporating AI-generated content, deepfake impersonation, and sophisticated social engineering…
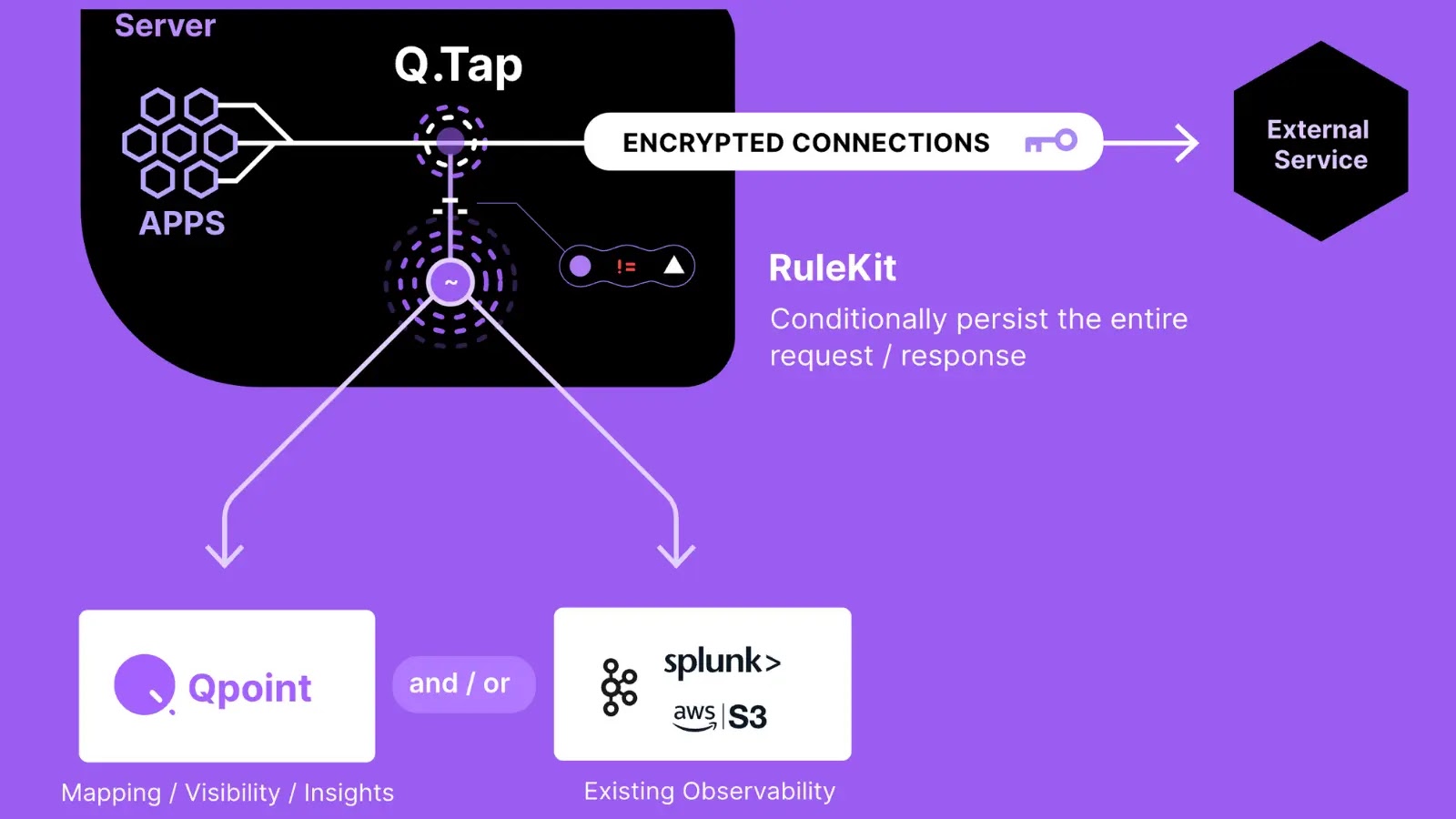
Qpoint has released Qtap, an open-source eBPF agent for monitoring network traffic in Linux systems. It hooks into TLS/SSL functions…
A severe security vulnerability has been identified in ManageEngine Exchange Reporter Plus that could allow attackers to execute arbitrary commands…
SAP released its monthly Security Patch Day update addressing 14 critical vulnerabilities across multiple enterprise products. The comprehensive security update…
Sensata Technologies, Inc., a prominent industrial technology company based in Attleboro, Massachusetts, has disclosed a significant cybersecurity incident that compromised…
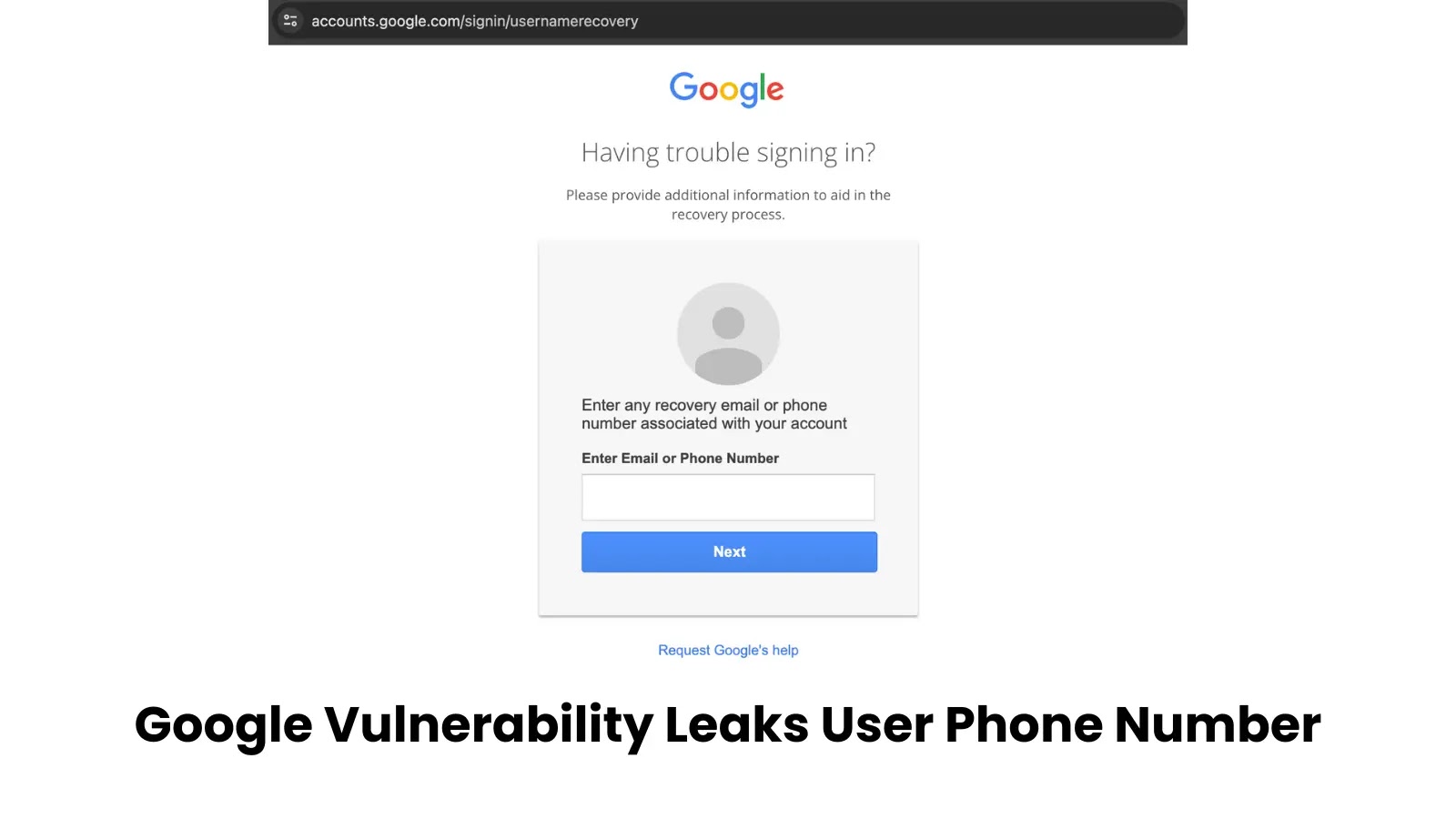
A critical security vulnerability in Google’s account recovery system allowed malicious actors to obtain the phone numbers of any Google…
A recent campaign by Chinese state-sponsored threat actor APT41 has unveiled a novel exploitation of Google Calendar for malware command-and-control…
Chinese state-sponsored hackers launched sophisticated reconnaissance operations against cybersecurity giant SentinelOne’s infrastructure in October 2024, representing part of a broader…