Category: CyberSecurityNews
A sophisticated scam operation dubbed “GhostVendors” that exploits over 4,000 fraudulent domains to impersonate dozens of major brands and defraud…
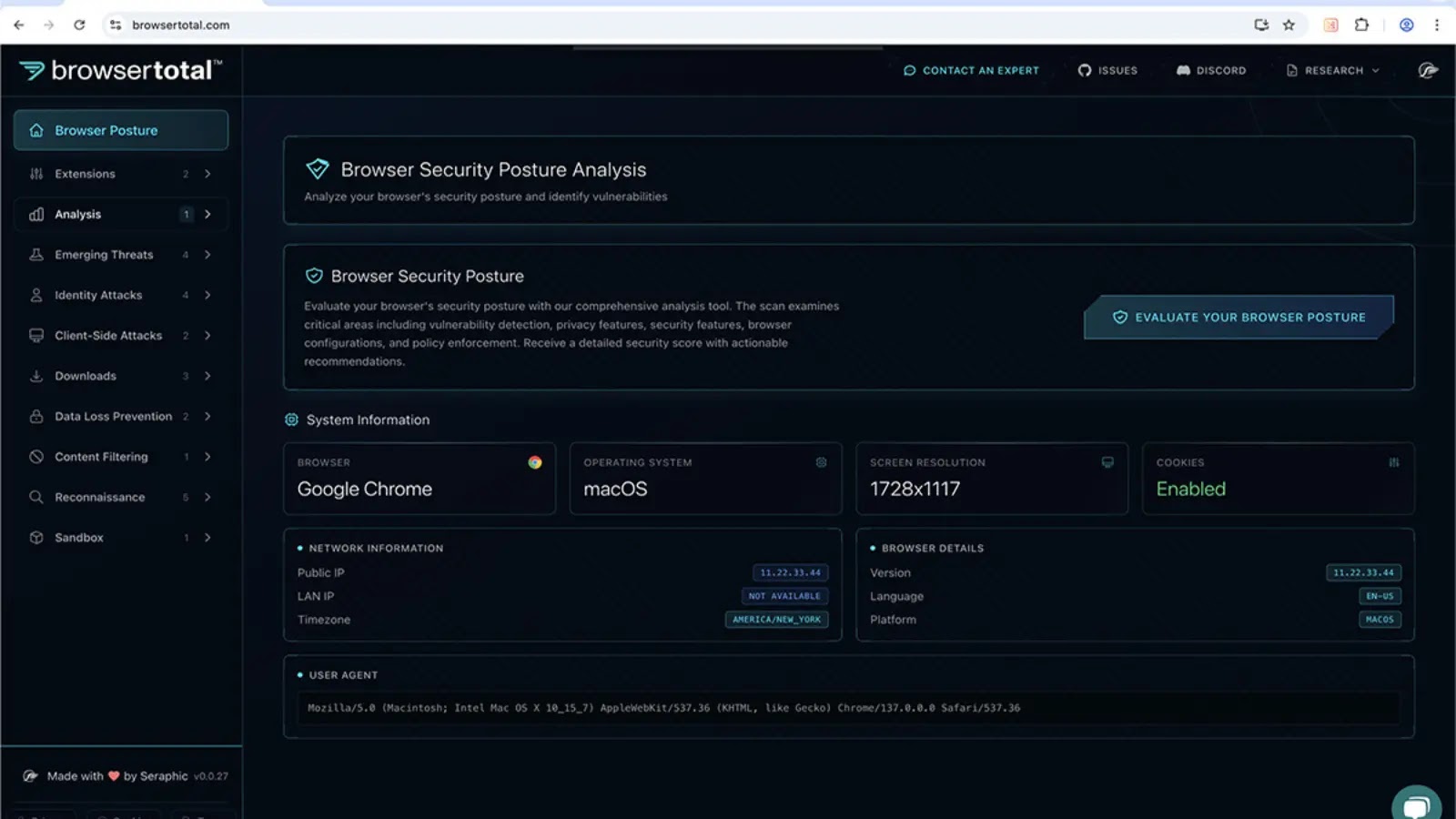
Tel Aviv, Israel, June 9th, 2025, CyberNewsWire Available to the public and debuting at the Gartner Security & Risk Management…
A new wave of cyberattacks has emerged targeting critical infrastructure through the exploitation of Fortigate security appliance vulnerabilities, with threat…
In recent months, a new wave of sophisticated malware campaigns has swept through millions of devices worldwide, driven by an…
Windows 11’s latest 24H2 update has inadvertently broken a widely-used malware evasion technique known as the Lloyd Labs self-delete method,…
Arkana Security Group claims to have successfully gained access to Ticketmaster’s database infrastructure and exfiltrated massive volumes of sensitive customer…
A critical zero-day vulnerability discovered in Salesforce‘s default controller has exposed millions of user records across thousands of deployments worldwide. …
A sophisticated new malware attack vector that manipulates users through fake browser verification prompts designed to mimic legitimate CAPTCHA systems. …
A new proof-of-concept (PoC) exploit for a critical zero-day vulnerability affecting multiple Fortinet products raises urgent concerns about the security…
Kali GPT, a specialized AI model built on GPT-4 architecture, has been specifically developed to integrate seamlessly with Kali Linux,…
A sophisticated new information-stealing malware written in the Rust programming language has emerged, demonstrating advanced capabilities to extract sensitive data…
Cybersecurity researchers have identified a sophisticated new social engineering campaign that exploits fundamental human trust in everyday computer interactions. The…