Category: CyberSecurityNews
As enterprises race to embrace digital transformation, many find themselves shackled to legacy systems—aging yet mission-critical technologies that power core…
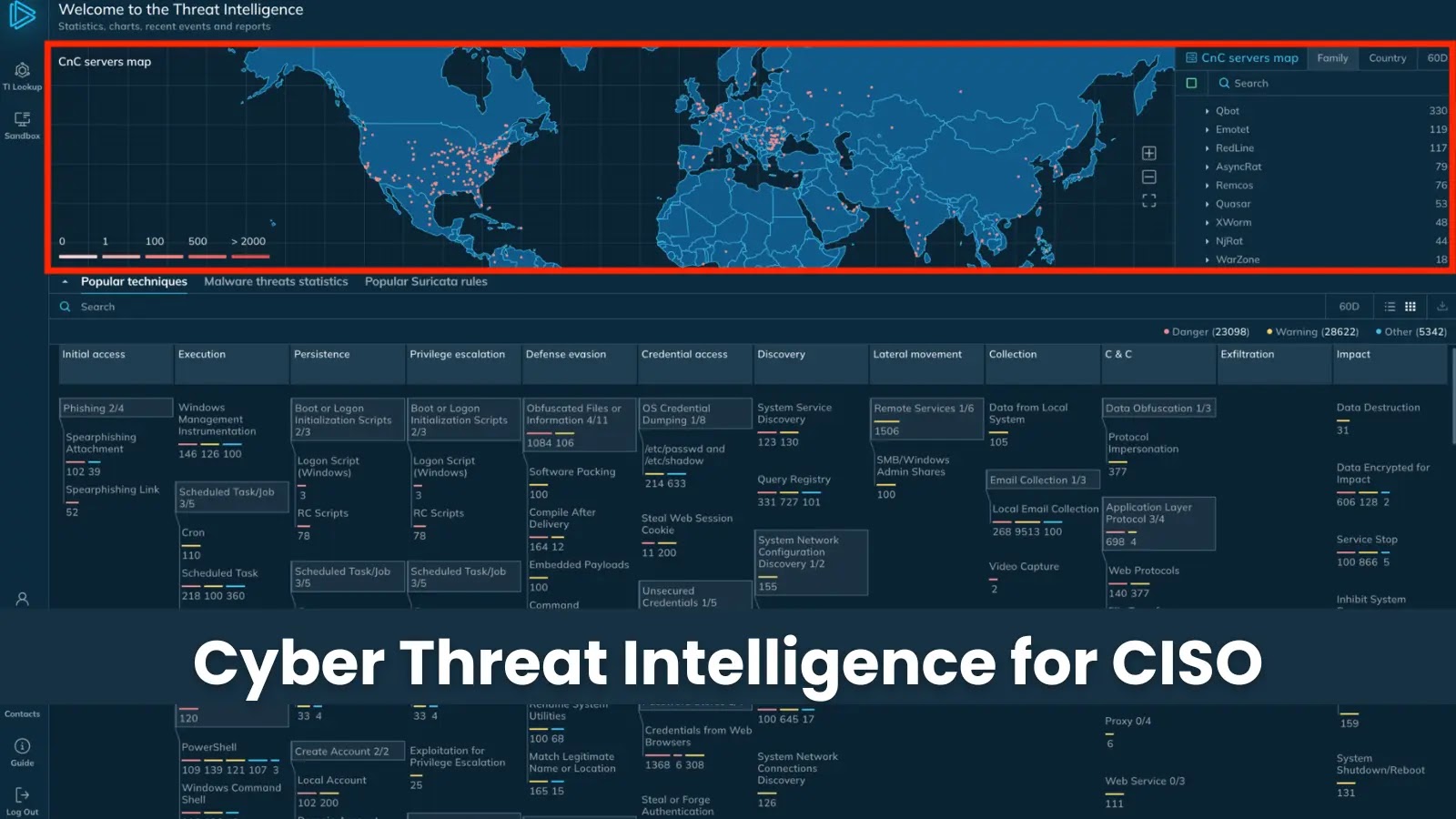
Cyber threat intelligence (CTI) is the practice of collecting, analyzing, and transforming data about cyber threats into actionable insights to…
Aembit, the workload identity and access management (IAM) company, today announced a major expansion of its platform to support Microsoft…
Microsoft Edge for Android is rolling out an enhanced privacy feature that allows users to secure their InPrivate browsing sessions…
A high-severity vulnerability was uncovered in Splunk Universal Forwarder for Windows that compromises directory access controls. The flaw, designated CVE-2025-20298…
A new cross-site scripting (XSS) vulnerability in Safari that exploits the browser’s TypeError exception handling mechanism to execute arbitrary JavaScript…
Cybercriminals have launched a sophisticated campaign targeting travelers through fake Booking.com websites that deploy AsyncRAT malware, according to recent security…
A sophisticated cryptocurrency theft campaign has emerged on the npm package registry, targeting developers and cryptocurrency users through malicious packages…
A significant vulnerability, CVE-2025-26396, affects the SolarWinds Dameware Mini Remote Control Service could allow attackers to escalate privileges on affected…
A significant denial of service vulnerability has been discovered in ModSecurity, one of the most widely deployed open-source web application…
Multiple security vulnerabilities in Hewlett-Packard Enterprise (HPE) StoreOnce software platform that could allow remote attackers to execute malicious code, bypass…
A significant security vulnerability in the Splunk Enterprise platform could allow low-privileged attackers to execute unauthorized JavaScript code through a…