Category: CyberSecurityNews
In 2025, the exploitation of supply chain vulnerabilities by Advanced Persistent Threats (APTs) has emerged as one of the most…
The cybersecurity landscape of 2025 has become a high-stakes battleground as Advanced Persistent Threat (APT) campaigns leverage artificial intelligence, zero-day…
A sophisticated botnet campaign dubbed “AyySSHush” has compromised over 9,000 ASUS routers worldwide, establishing persistent backdoor access that survives firmware…
A critical security flaw in Microsoft’s OneDrive File Picker has exposed millions of users to unauthorized data access, allowing third-party…
Cybersecurity researchers have uncovered a sophisticated new attack method called “ChoiceJacking” that allows malicious charging stations to steal sensitive data…
As 2025 unfolds, the digital battleground has never been more complex-or more consequential. Cyberattacks are no longer isolated incidents but…
Zscaler Inc. announced on May 27, 2025, a definitive agreement to acquire Red Canary, a leading Managed Detection and Response…
Cybercriminals leveraged critical vulnerabilities in remote monitoring software to breach a managed service provider and attack multiple customers. Cybersecurity researchers…
A critical security vulnerability in the popular TI WooCommerce Wishlist plugin has left over 100,000 WordPress websites exposed to potential…
Security researchers have uncovered a significant cybercrime operation involving 93.7 billion stolen browser cookies circulating on dark web marketplaces, representing…
As the digital threat landscape intensifies and new technologies reshape business operations, cybersecurity budgeting in 2025 will be significantly transformed….
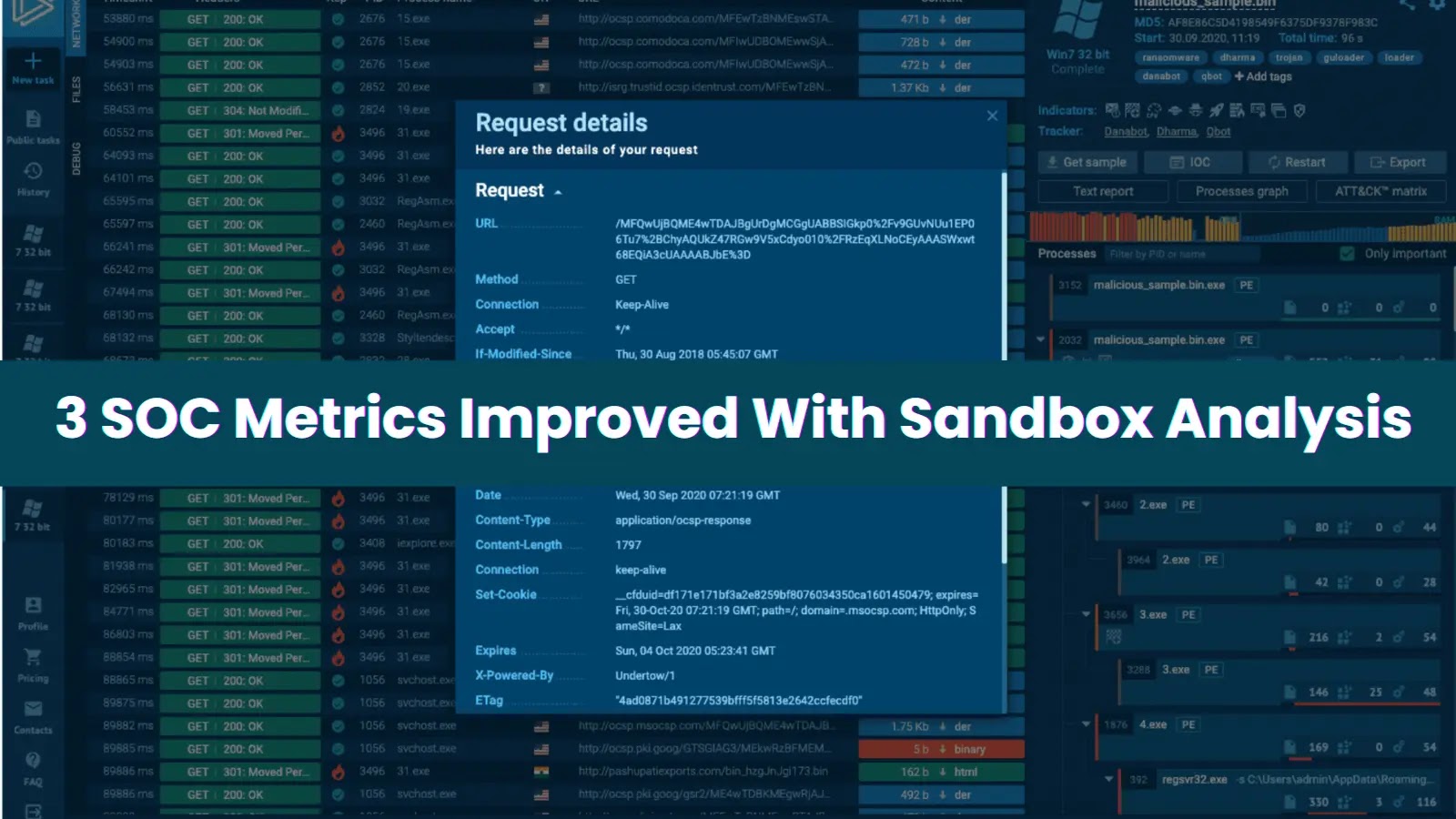
SOC teams are flooded with alerts, but what really matters is how quickly they can detect, investigate, and respond. When…