Category: CyberSecurityNews
Cisco disclosed a high-severity vulnerability affecting its Identity Services Engine (ISE) that could allow unauthenticated remote attackers to cause a…
Apple’s Lockdown Mode offers an extreme security level for users who may be targeted by sophisticated cyberattacks. While most iPhone…
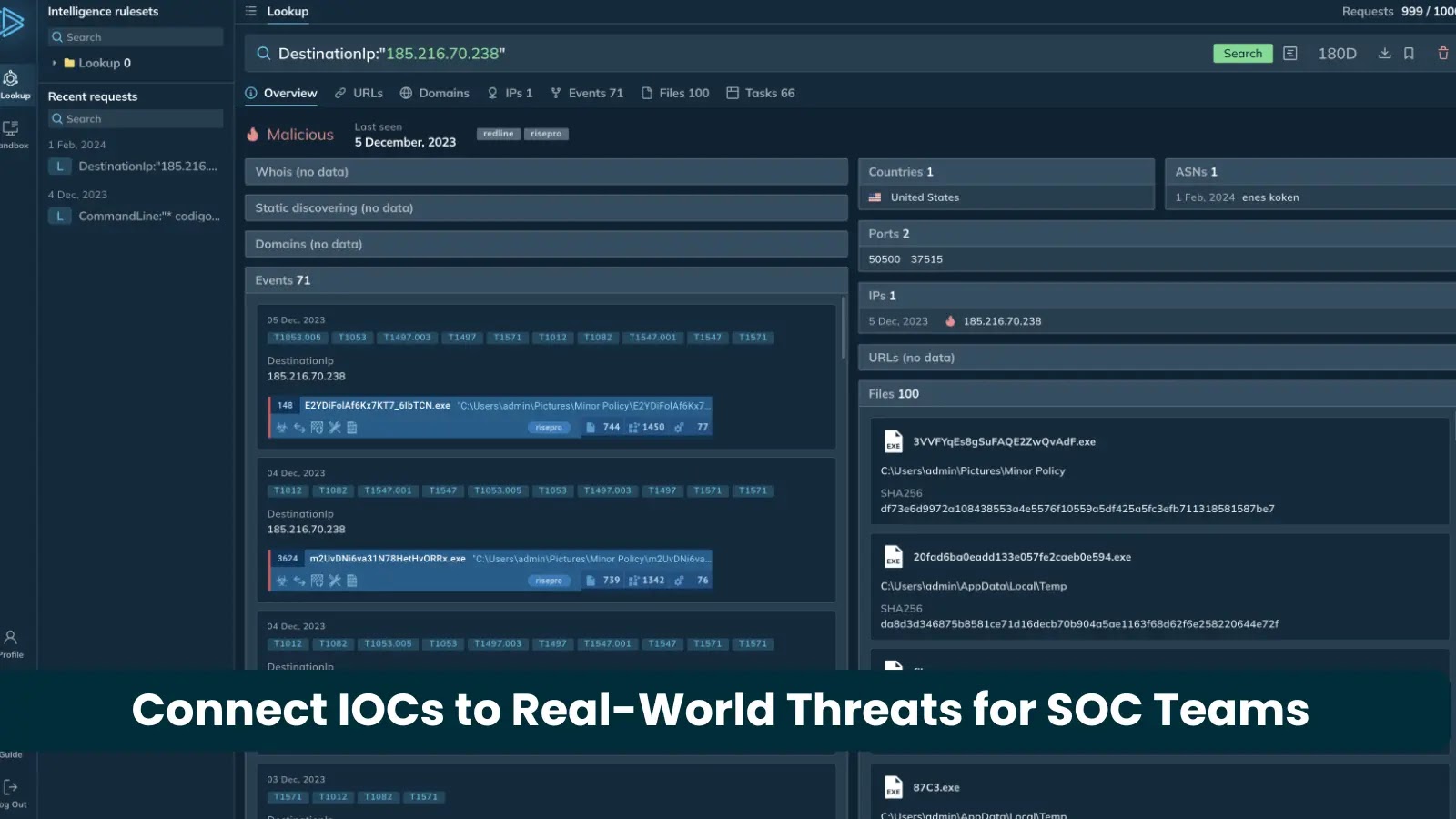
When it comes to cyber threats, data alone isn’t enough. Security Operations Center (SOC) teams are flooded with indicators of…
The Tor Project has announced the release of Tor Browser 14.5.2, available since May 18, 2025. This latest version delivers…
A critical security vulnerability in ChatGPT has been discovered that allows attackers to embed malicious SVG (Scalable Vector Graphics) and…
Security researchers have discovered a new technique to bypass Kernel Address Space Layout Randomization (KASLR) in Windows 11, potentially weakening…
In today’s digital landscape, cybercrime has undergone a dramatic transformation. No longer limited to skilled hackers, cyberattacks are now available…
A sophisticated malware strain called ModiLoader (also known as DBatLoader) has emerged as a significant threat to Windows users, specifically…
A critical vulnerability in the GNU C Library (glibc), potentially exposing millions of Linux systems to local privilege escalation attacks. …
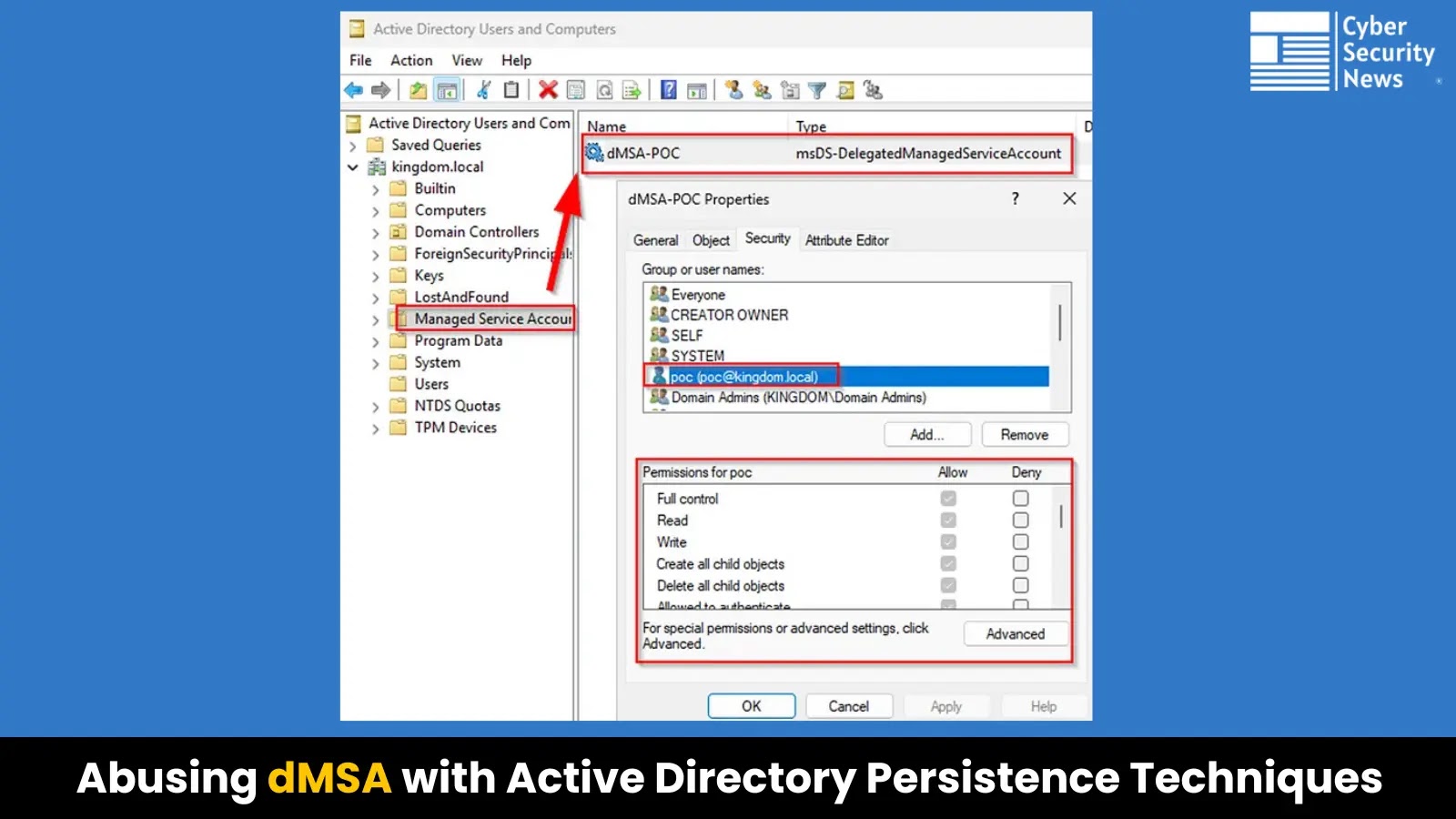
Delegated Managed Service Accounts (dMSAs), introduced in Windows Server 2025, represent Microsoft’s latest innovation in secure service account management. While…
A critical vulnerability in Microsoft’s Remote Desktop Gateway (RD Gateway) that could allow attackers to execute malicious code on affected…
A new information-stealing malware dubbed “PupkinStealer” has been identified by cybersecurity researchers, targeting sensitive user data through a straightforward yet…