Category: CyberSecurityNews
A severe privilege escalation vulnerability has been discovered in Notepad++ version 8.8.1, potentially exposing millions of users worldwide to complete…
Summary 1. CVE-2025-49825 allows attackers to remotely bypass Teleport’s authentication controls, affecting multiple versions of the secure access platform. 2. Teleport…
Five dedicated bug bounty programs upgraded across 1inch core components, including smart contracts, wallet and infrastructure. A community-first approach to…
Summary 1. Harmful Objective Concealed: Attacker defines a harmful goal but starts with benign prompts. 2. Context Poisoning: Introduces subtle…
The OpenSSL Corporation and the OpenSSL Foundation are issuing a final call for speaker proposals for the inaugural OpenSSL Conference 2025, taking place October 7–9, 2025, at the Vienna…
McLaren Health Care, a major healthcare organization based in Grand Blanc, Michigan, has disclosed a significant data breach that compromised…
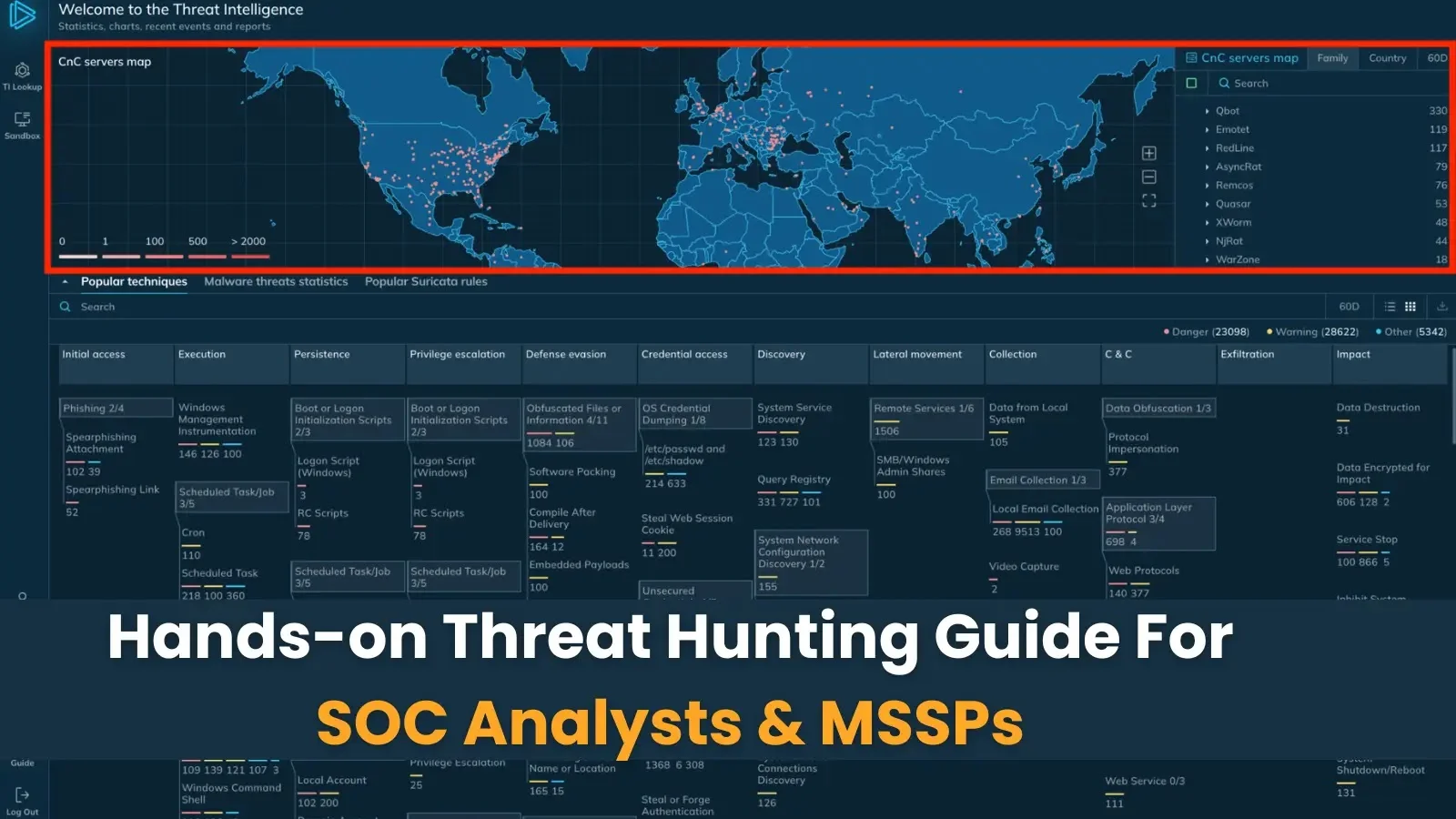
This comprehensive guide provides SOC analysts and MSSP teams with practical threat hunting techniques using advanced threat intelligence platforms. Modern…
Ukrainian government agencies have fallen victim to a sophisticated cyberattack campaign orchestrated by the UAC-0001 group, also known as APT28,…
Summary 1. Microsoft Defender for Office 365 is introducing large language model (LLM) technology to provide clear, human-readable explanations for…
Summary 1. IPFire 2.29 Core Update 195 now includes fully integrated WireGuard protocol with web UI management, supporting both net-to-net…
A Pakistan-based cyber espionage group known as APT36 or Transparent Tribe has launched a highly sophisticated phishing campaign targeting Indian…
Summary 1. CoinMarketCap discovered a security flaw on June 20, 2025, in a homepage doodle image that executed malicious code…