Category: CyberSecurityNews
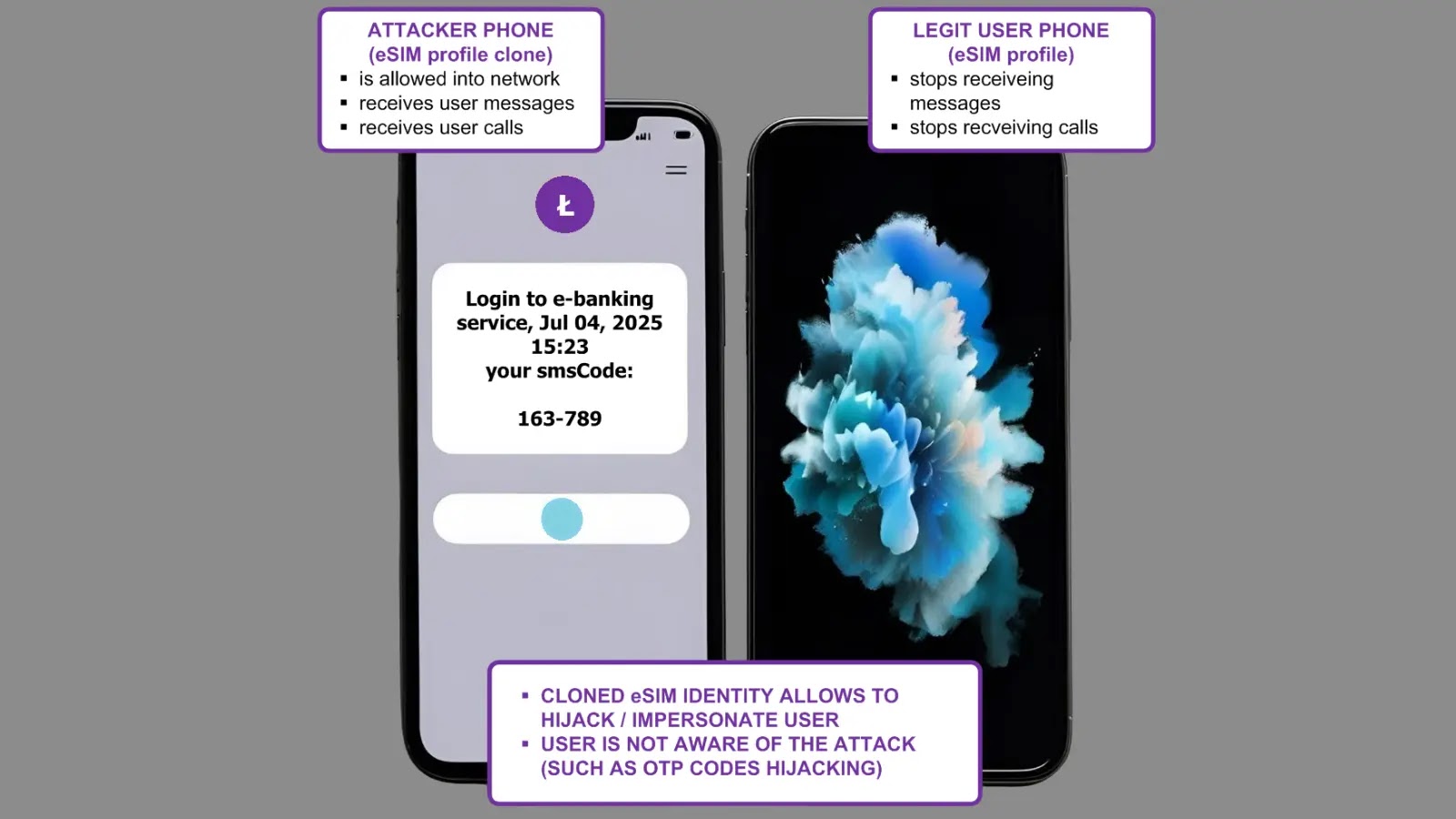
A critical vulnerability in eSIM technology enables attackers to clone mobile subscriber profiles and hijack phone identities. AG Security Research…
The Apache Software Foundation has released Apache HTTP Server version 2.4.64, addressing eight critical security vulnerabilities that affected versions spanning…
A Russian professional basketball player has been arrested in France on charges of orchestrating one of the most extensive ransomware…
Advanced Micro Devices has disclosed a series of critical security vulnerabilities affecting multiple generations of its processor architectures, stemming from…
The Rockerbox breach burst onto the threat-intelligence radar in early July 2025 when an unencrypted, 286.9 GB cloud repository holding…
A critical vulnerability in Laravel applications exposes APP_KEY configuration values, enabling attackers to achieve remote code execution (RCE). Collaborative research…
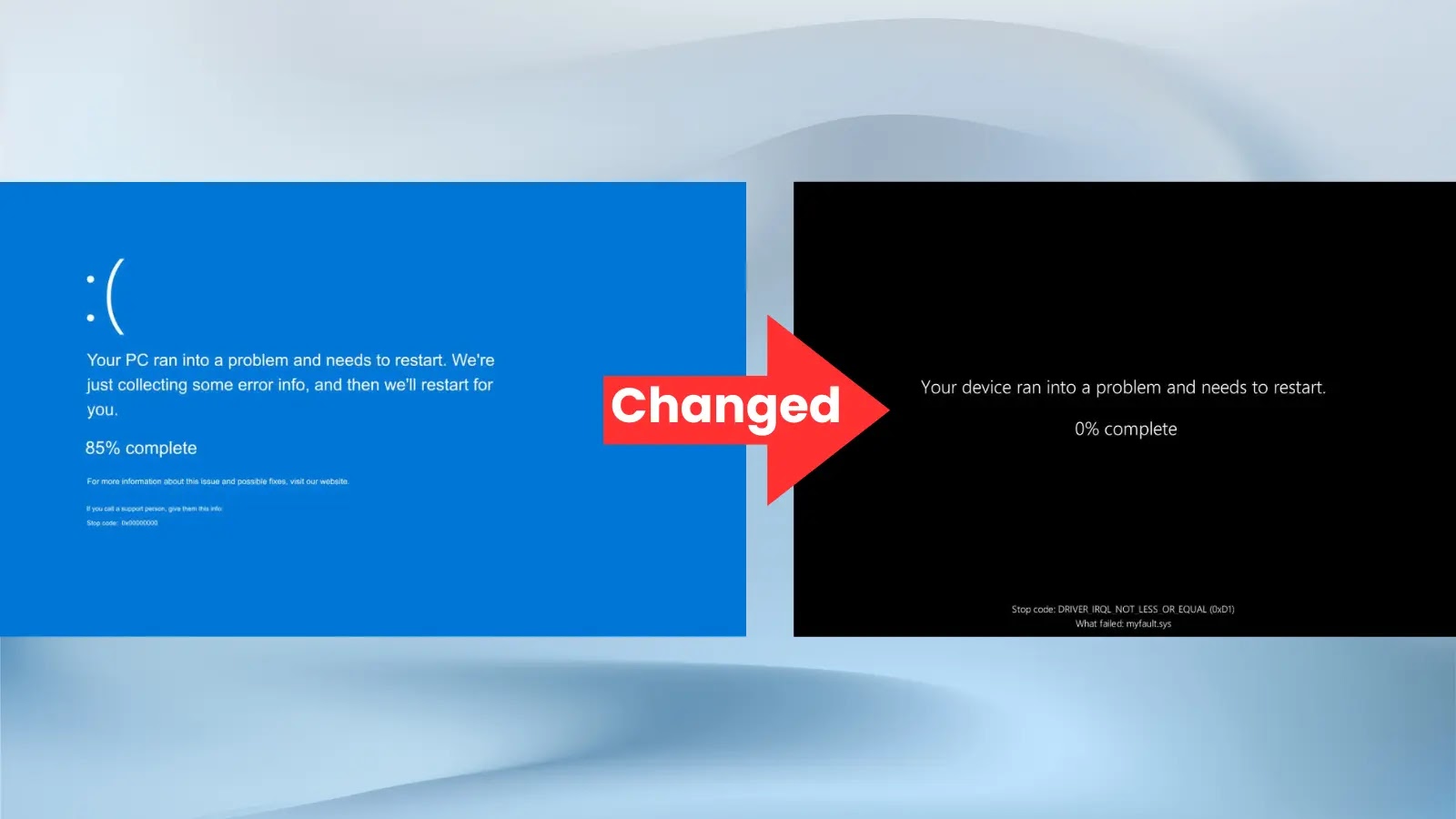
Microsoft has begun rolling out a redesigned error screen interface as part of Windows 11 Build 26100.4762, introducing what users…
A sophisticated new variant of the macOS.ZuRu malware has emerged, targeting macOS users through a weaponized version of the popular…
A sophisticated cybercrime operation has successfully stolen $500,000 in cryptocurrency assets from a Russian blockchain developer through a malicious extension…
The cybersecurity landscape continues to evolve with increasingly sophisticated malware variants, and a recent discovery highlights the persistent threat posed…
A new ransomware threat has emerged as one of the most formidable adversaries in the cybersecurity landscape, demonstrating unprecedented growth…
Schneider Electric has disclosed a critical set of six vulnerabilities affecting its EcoStruxure IT Data Center Expert software that could…