Category: CyberSecurityNews
The cybersecurity landscape is witnessing a growing complexity in the attribution of Advanced Persistent Threat (APT) actors, particularly the North…
Dell Technologies has released a critical security update addressing multiple severe vulnerabilities in its Unity enterprise storage systems that could…
A critical vulnerability (CVE-2025-2825) in CrushFTP, a widely used enterprise file transfer solution, allows attackers to bypass authentication and gain…
Canon has issued a critical security advisory regarding a severe vulnerability detected in several of its printer drivers that could…
Security researchers have published a detailed technical analysis of a critical remote code execution (RCE) vulnerability (CVE-2023-38408) in OpenSSH’s agent…
A critical vulnerability in PHP’s libxml streams has been identified, potentially impacting web applications that rely on the DOM or…
A sophisticated social engineering technique known as ClickFix has emerged, leveraging fake CAPTCHA verification processes to deceive users into executing…
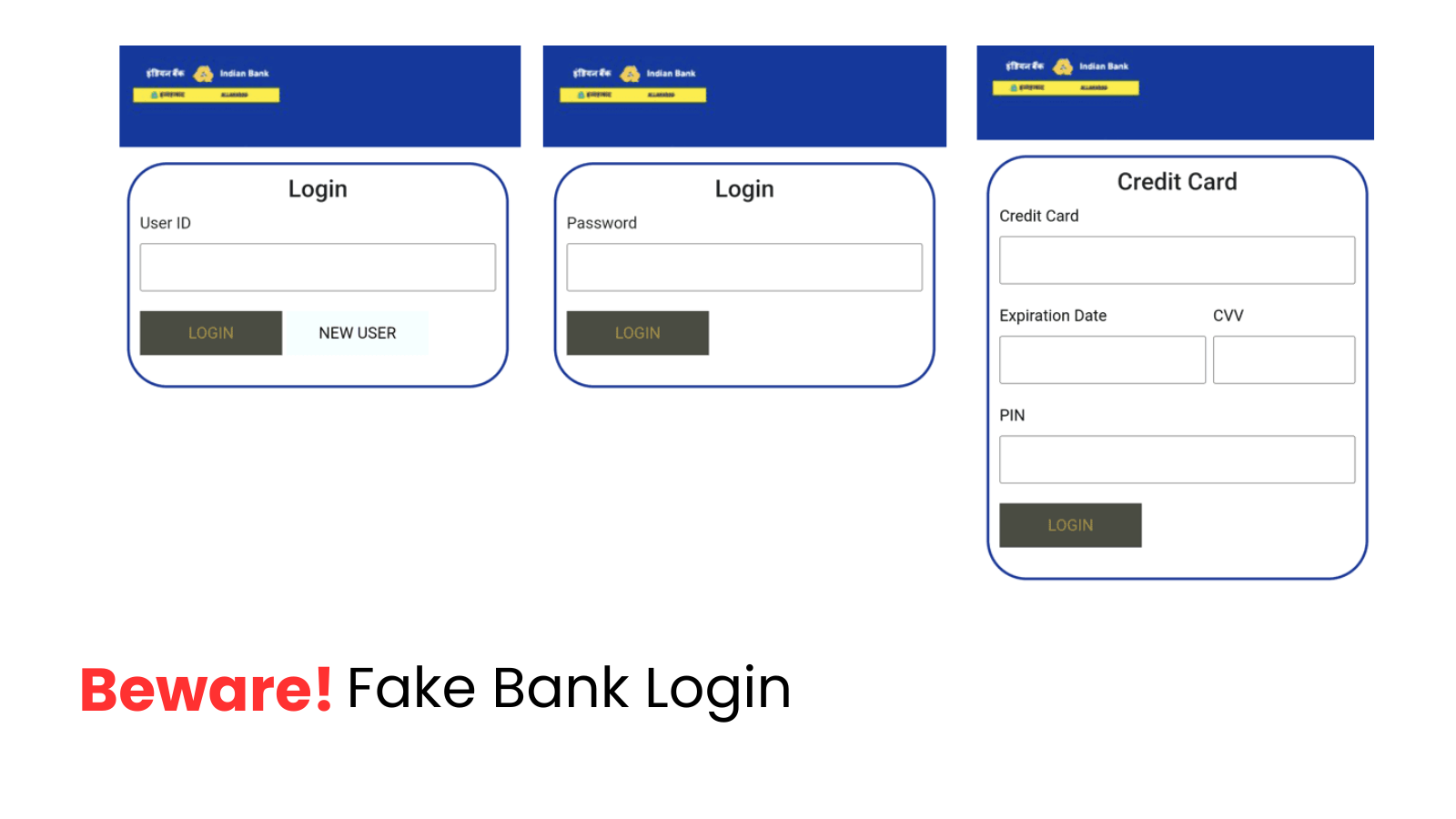
A newly discovered Android banking malware named TsarBot is targeting over 750 applications globally, including banking, finance, cryptocurrency, and e-commerce…
A critical vulnerability in Apache Tomcat has been actively exploited by attackers to achieve remote code execution (RCE) on vulnerable…
The Lotus Blossom Advanced Persistent Threat (APT) group, also known as Lotus Panda, Billbug, and Spring Dragon, has intensified its…
The Cybersecurity and Infrastructure Security Agency (CISA) has issued a Malware Analysis Report (MAR-25993211-r1.v1) detailing the exploitation of a critical…
Disney’s latest release, Snow White (2025), has turned into a cybersecurity crisis for unsuspecting users. With a disappointing IMDb rating…