Category: CyberSecurityNews
Cybercriminals recently exploited Google’s g.co subdomain to carry out a meticulously crafted scam over a vishing call. The incident was…
Cybercriminals are increasingly exploiting vulnerabilities in government websites to carry out phishing campaigns, leveraging the inherent trust users place in…
Researchers have uncovered two critical vulnerabilities in Apple’s custom silicon chips, dubbed SLAP (Speculative Load Address Prediction) and FLOP (False…
The state-sponsored threat actors are increasingly exploiting Google’s AI-powered assistant, Gemini, to enhance their cyber operations. While generative AI tools…
The most recent update for Windows 11 24H2, identified as KB5050009, has caused various kinds of technical issues for users,…
Microsoft 365 users worldwide encountered significant disruptions today as multiple services, including the Microsoft 365 Admin Center, reported degradation or…
A Cross-Site Scripting (XSS) vulnerability has been identified in the TP-Link Archer A20 v3 router, specifically in firmware version 1.0.6…
A significant zero-day vulnerability in Zyxel CPE series devices, identified as CVE-2024-40891, is being actively exploited by attackers. This vulnerability…
DeepSeek R1, the latest AI model from China, is making waves in the tech world for its reasoning capabilities. Positioned…
Phemex, a cryptocurrency exchange based in Singapore, suffered a significant cyberattack that resulted in the theft of $85 million worth…
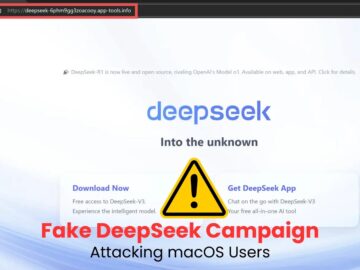
A new cyberattack campaign, dubbed the “Fake DeepSeek Campaign,” has been discovered targeting macOS users. DeepSeek, a Chinese-developed AI chatbot, has…
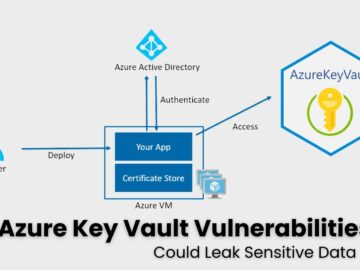
A detailed walkthrough demonstrates how attackers can manipulate Azure Key Vault’s access policies after compromising Entra ID (formerly Azure AD)…