Category: CyberSecurityNews
Cloudflare recently thwarted the largest distributed denial-of-service (DDoS) attack ever recorded, peaking at an unprecedented 5.6 terabits per second (Tbps)….
Microsoft and OpenAI have announced an extension and evolution of their strategic partnership, reinforcing their commitment to advancing artificial intelligence…
As artificial intelligence (AI) continues its meteoric rise, 2025 is shaping up to be a transformative year in the realm…
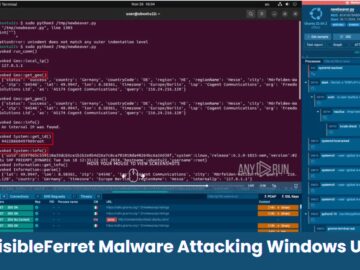
A new wave of North Korean cyberattacks, employing a sophisticated and coordinated approach, has targeted the technology, financial, and cryptocurrency…
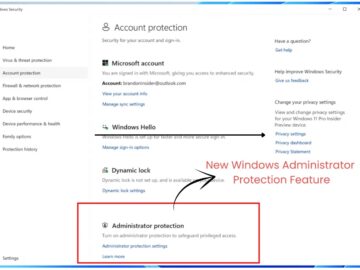
Microsoft has unveiled a groundbreaking security feature called Administrator Protection, now available to Windows Insiders in the Canary Channel with…
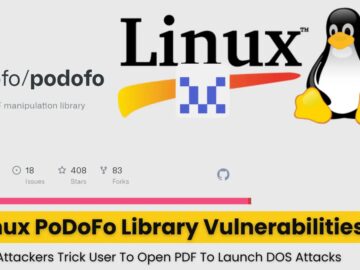
Canonical’s Ubuntu Security Team has announced fixes for multiple vulnerabilities affecting the PoDoFo library, a popular PDF manipulation library, in…
A sophisticated cyberattack campaign targeting German organizations has been uncovered, utilizing weaponized LNK files to deploy the Sliver implant. The…
Multiple critical vulnerabilities have been discovered in HPE Aruba Network, affecting its AOS Controllers, Gateways, and Mobility Conductor products. Specifically,…
A newly identified Internet of Things (IoT) botnet has been orchestrating large-scale Distributed Denial-of-Service (DDoS) attacks globally since late 2024,…
Threat actor IntelBroker allegedly breached Hewlett Packard Enterprise (HPE) and claimed responsibility for the intrusion on a dark web forum….
A significant cybersecurity threat involving North Korean hackers exploiting LinkedIn as an entry point to infiltrate organizations. This attack has…
A sophisticated Android malware campaign targeting users in South Asia, particularly in the Kashmir region of India has been recently…