Category: CyberSecurityNews
Cybersecurity firm Arctic Wolf has disclosed details of an ongoing cyber campaign targeting Fortinet FortiGate firewall devices with exposed management…
A new ransomware campaign has surfaced, leveraging Amazon Web Services’ (AWS) Server-Side Encryption with Customer Provided Keys (SSE-C) to encrypt…
Nominet, the official registry for .uk domain names and one of the largest country code registries globally has disclosed a…
OneBlood, a major blood donation nonprofit serving the southeastern United States, has confirmed a significant data breach resulting from a…
The Cybersecurity and Infrastructure Security Agency (CISA) has updated its Known Exploited Vulnerabilities (KEV) Catalog with two new critical vulnerabilities,…
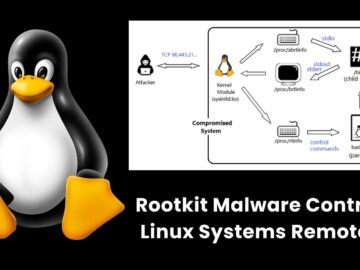
Fortinet researchers uncovered an advanced rootkit malware exploiting multiple zero-day vulnerabilities in enterprise appliances by executing a shell script (Install.sh)….
Microsoft Threat Intelligence has identified a significant vulnerability in macOS that could allow attackers to bypass Apple’s System Integrity Protection…
The Cybersecurity and Infrastructure Security Agency (CISA) has added a critical OS command injection vulnerability (CVE-2024-12686) found in BeyondTrust’s Privileged…
The U.S. Cybersecurity and Infrastructure Security Agency (CISA) has launched a new guidance document to enhance cybersecurity for operational technology…
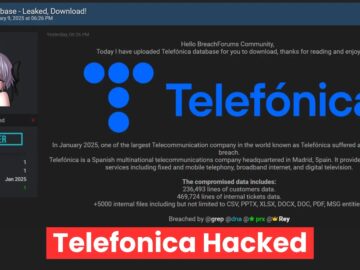
Spanish telecommunications giant Telefonica has confirmed a significant breach of its internal systems, with attackers claiming to have stolen approximately…
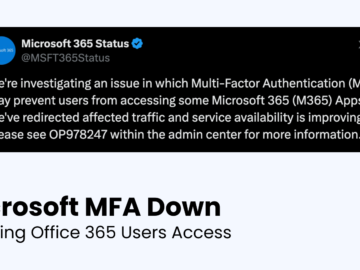
Microsoft has alerted users to an issue with its Multi-Factor Authentication (MFA) system, which has disrupted access to certain Microsoft…
A critical remote code execution (RCE) vulnerability, CVE-2024-50603, has been actively exploited in the wild, posing significant risks to cloud…