Category: CyberSecurityNews
Amazon Web Services (AWS) has introduced the same remote code execution (RCE) vulnerability three times over the last four years…
A critical Windows Registry Elevation of Privilege vulnerability, identified as CVE-2024-43641. This flaw, which affects various editions of Windows Server…
On Friday, the U.S. Department of the Treasury announced sanctions against Integrity Technology Group, a Beijing-based cybersecurity firm accused of…
Nikki-Universal Co. Ltd., a prominent chemical manufacturer, has fallen victim to a sophisticated ransomware attack. The incident, which the company…
ASUS, a leading networking equipment manufacturer, has issued a critical security advisory for several router models. The company has identified…
Federal authorities have unsealed an indictment against a U.S. Army soldier, accusing him of selling and attempting to sell stolen…
A malicious npm campaign that poses as the Hardhat plugins and the Nomic Foundation is observed to target Ethereum developers…
Security researchers have uncovered a novel attack targeting macOS systems running on Apple Silicon processors. Dubbed “SysBumps,” this attack exploits…
The Office for Civil Rights (OCR) at the U.S. Department of Health and Human Services (HHS) has unveiled a Notice…
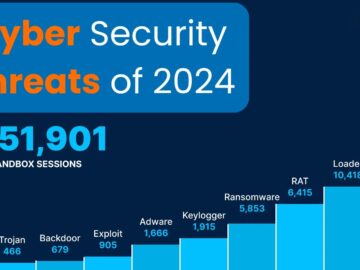
As 2024 concludes, cybersecurity experts are reflecting on an eventful Q4 that witnessed evolving threats and heightened activity in the…
German authorities have charged three Russian-German nationals with espionage and sabotage activities aimed at undermining Germany’s military support for Ukraine….
A new ransomware strain, dubbed Nitrogen, has emerged as a significant threat over the past four months, targeting organizations across…