Category: CyberSecurityNews
The much-anticipated final release of Kali Linux for 2024.4 is here, packed with many updates, new hacking tools, and powerful…
The Cybersecurity and Infrastructure Security Agency (CISA) has added two new vulnerabilities to its Known Exploited Vulnerabilities Catalog, one of…
In a significant move that will reshape the cybersecurity landscape, Arctic Wolf and BlackBerry Limited (NYSE: BB; TSX:BB) announced today…
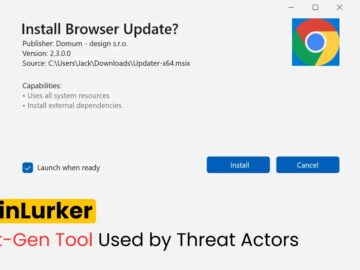
CoinLurker is a sophisticated data-stealing malware that has revolutionized fake update campaigns. Written in the Go programming language, CoinLurker incorporates…
Hackers leveraged Microsoft Teams to manipulate a victim into granting remote access to their system. The attack, analyzed by Trend…
A new wave of cyberattacks has emerged, targeting YouTube creators through malicious collaboration requests that exploit the trust between creators…
A critical Remote Code Execution (RCE) vulnerability has been discovered in a popular open-source biomedical tool used worldwide. This vulnerability,…
Serbian police and intelligence services have been reported to use advanced phone spyware in conjunction with mobile forensic tools to…
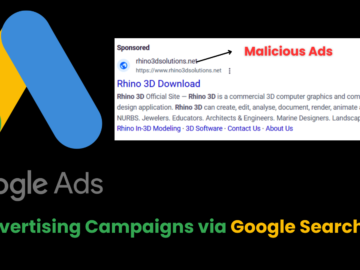
Threat researchers have identified a persistent series of malvertising campaigns targeting graphic design professionals, using Google Search ads as a…
Security researchers have uncovered several high-severity vulnerabilities in the popular Mullvad VPN service that could allow attackers to execute malicious…
Welcome to this week’s Cyber Security Newsletter, where we delve into the latest developments and crucial updates in cybersecurity. Your…
A critical security flaw has been discovered in the popular data transfer tool Curl, potentially allowing attackers to access sensitive…