Category: CyberSecurityNews
The Open Source Security Foundation (OpenSSF) has launched the Open Source Project Security Baseline (OSPS Baseline), a tiered framework designed…
Cisco Systems has issued a critical security advisory addressing a command injection vulnerability in its Nexus 3000 and 9000 Series…
A new attack dubbed nRootTag has exposed over 1.5 billion Apple devices, including iPhones, iPads, Apple Watches, and Macs, to…
The U.S. Cybersecurity and Infrastructure Security Agency (CISA) issued an urgent advisory on February 25, 2025, confirming that threat actors…
A sophisticated malware campaign dubbed “GitVenom” has exploited GitHub’s open-source ecosystem to distribute malicious code through thousands of fraudulent repositories,…
A critical server-side request forgery (SSRF) vulnerability (CVE-2025-27090) has been identified in the Sliver C2 framework’s teamserver implementation, enabling attackers…
A sophisticated threat cluster tracked as UAC-0212 has escalated efforts to compromise critical infrastructure systems in Ukraine, according to a…
The LightSpy advanced persistent threat (APT) group has significantly upgraded its surveillance capabilities with a 100+ command framework targeting Android,…
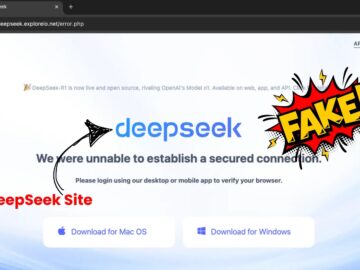
Cybersecurity researchers uncovered a sophisticated macOS malware campaign distributing the Poseidon Stealer through a counterfeit DeepSeek AI platform website. This…
INE, the leading provider of networking and cybersecurity training and certifications, today announced its recognition as an enterprise and small…
In an era where open-source collaboration drives software innovation, a sophisticated cyber campaign dubbed GitVenom has emerged as a critical…
A coordinated campaign involving at least 16 malicious Chrome extensions infected over 3.2 million users worldwide, leveraging browser security vulnerabilities…