Category: CyberSecurityNews
A sophisticated malware campaign employing steganographic techniques has recently been identified, targeting users through seemingly innocent JPEG image files. The…
A severe vulnerability in the Linux kernel has remained undetected for nearly two decades, allowing local users to gain root…
A sophisticated attack vector dubbed “MalDoc in PDF” allows threat actors to bypass traditional security scanning by embedding malicious Word…
Password reuse continues to be one of the most significant security vulnerabilities in 2025, with alarming new data showing nearly…
California Cryobank LLC, one of America’s largest sperm donor repositories, has confirmed a significant data breach that exposed sensitive customer…
A sophisticated attack employing Legacy Driver Exploitation technique has emerged as a significant cybersecurity threat, according to a recent security…
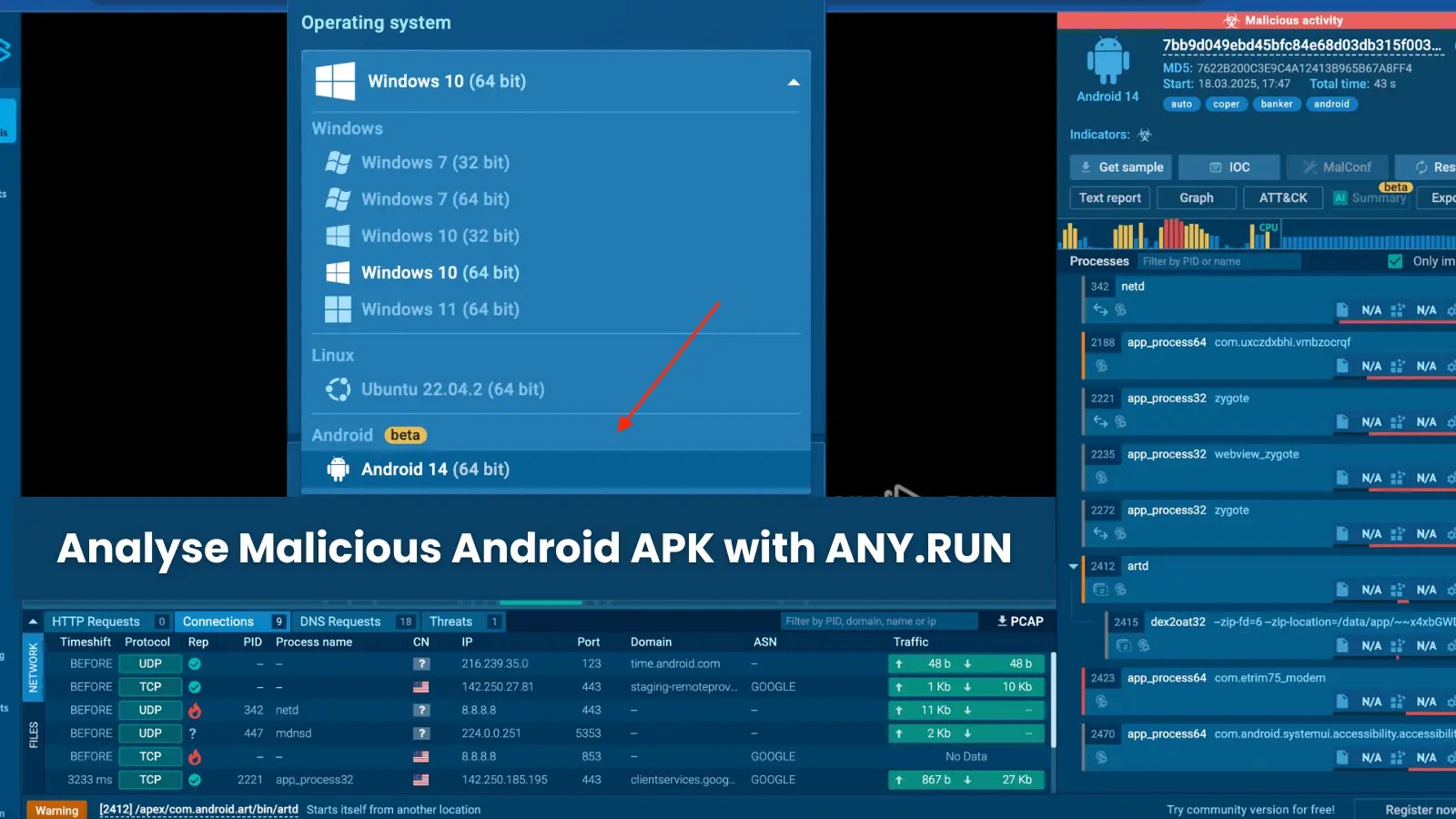
ANY.RUN, the interactive malware analysis platform has announced full support for Android OS in its cloud-based sandbox environment, enabling security…
Cybersecurity experts have identified a persistent trend of threat actors exploiting legitimate remote monitoring and management (RMM) software to infiltrate…
Moving Beyond Detection to Real-Time, Automated Security Across Workloads, Cloud, and Infrastructure SecPod, a global cybersecurity provider, has announced the…
Kali Linux, the widely acclaimed cybersecurity-focused distribution, has officially unveiled its latest release, Kali Linux 2025.1a. This update not only significantly enhances desktop environments but also…
The China-aligned advanced persistent threat (APT) group MirrorFace has updated its tactics, techniques, and procedures (TTPs) with a sophisticated approach…
VPN infrastructure has become a prime target for cybercriminals and state-sponsored actors, with vulnerabilities in these systems serving as gateways…