Category: CyberSecurityNews
In an era where cloud deployment is becoming a necessity for developers, GitHub Copilot for Azure is transforming how developers…
In a rare occurrence, the Linux kernel development cycle has aligned favorably with the holiday season this year. Linus Torvalds,…
Notepad++ has released version 8.7.2 with a highly anticipated new feature “Pin Tab,” it’s a popular free source code editor…
A series of security vulnerabilities have been identified in MediaTek chipsets, affecting several Android versions and other related software platforms….
Amazon GuardDuty has launched advanced AI/ML threat detection capabilities, enhancing its ability to protect cloud environments from sophisticated security threats….
A critical remote code execution vulnerability in Apple Safari, identified as CVE-2024-44308, has been discovered and actively exploited in the…
Welcome to this week’s Cybersecurity Newsletter, where we delve into the latest advancements and critical updates in the cybersecurity landscape….
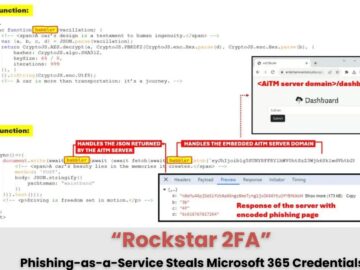
Cybersecurity researchers have identified a concerning link between the advanced phishing toolkit known as ‘Rockstar 2FA’ and a surge in…
Microsoft has announced plans to deprecate the “Bring Your Own License” (BYOL) feature in Microsoft Defender for Cloud as part…
A significant development for the tech community is the identification of 2 critical vulnerabilities in several versions of a widely-used…
In a recent study, cybersecurity researchers have unveiled a new side-channel attack that threatens the privacy of users interacting with…
Endpoint security has become a paramount concern for organizations of all sizes. With cyber threats becoming increasingly sophisticated and pervasive,…