Category: CyberSecurityNews
Russian-aligned hacking group RomCom has been discovered exploiting two critical zero-day vulnerabilities affecting Mozilla Firefox and Windows systems in a…
A sophisticated attack targeting npm users has been recently uncovered by the Socket’s threat research team in a concerning development…
A 31-year-old Kansas City man has been indicted on federal charges for allegedly hacking into the computer systems of a…
A significant security vulnerability has been discovered in Palo Alto Networks’ GlobalProtect app, potentially allowing attackers to escalate privileges on…
A critical vulnerability was discovered on October 30th, 2024 in the Anti-Spam by CleanTalk WordPress plugin, potentially affecting over 200,000…
A comprehensive Red Team Assessment (RTA) was conducted recently by the Cybersecurity and Infrastructure Security Agency (CISA) on a critical…
Seven critical vulnerabilities affecting Android and Google Pixel devices were recently uncovered during a recent analysis of mobile applications. These…
A ransomware attack on Blue Yonder, a critical supply chain management software provider, has forced Starbucks to revert to manual…
Multiple vulnerabilities have been identified in QNAP’s QuRouter, specifically affecting version 2.4.x. The vulnerabilities are tracked as CVE-2024-48860 and CVE-2024-48861,…
A malicious campaign has been discovered in which the malware employs a more nefarious tactic, dropping the legitimate Avast Anti-Rootkit…
The rapid growth of the internet and connected systems has revolutionized the way we communicate, work, and live. However, this…
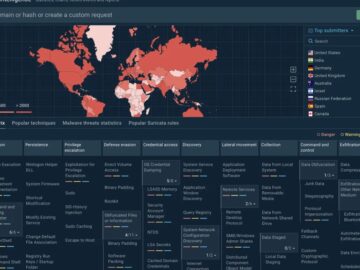
In a major update aimed at revolutionizing the way cybersecurity professionals tackle threats, ANY.RUN has unveiled its redesigned Threat Intelligence…