Category: CyberSecurityNews
The exponential growth of government data requests to technology giants has transformed Silicon Valley into the backbone of modern surveillance…
U.S. law enforcement announced the recovery of $31 million in cryptocurrency tied to the 2021 Uranium Finance exploit, marking one…
The United States has paused offensive cyber operations against Russia under an order from Defense Secretary Pete Hegseth, causing debates…
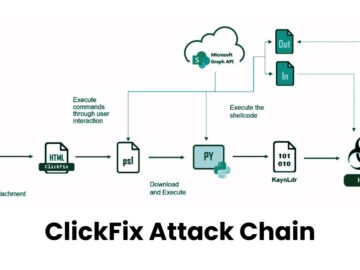
A sophisticated phishing campaign in which threat actors are utilizing a multi-stage attack chain that combines social engineering tactics with…
Google is advancing its email privacy arsenal with the development of Shielded Email, a feature designed to generate disposable email…
The cybersecurity landscape of 2024 witnessed an unprecedented increase in mass internet exploitation, driven by attackers’ ability to automate vulnerability…
Security researchers have uncovered three critical vulnerabilities in Extreme Networks’ IQ Engine (HiveOS) that collectively enable authenticated attackers to escalate…
Cybersecurity firm Silent Push have confirmed recently that North Korean IT workers continue to utilize Astrill VPN services to hide…
A major development in wireless security research has revealed a sophisticated Wi-Fi jamming technique capable of disabling individual devices with…
Authorities arrested a prolific hacker responsible for over 90 data breaches across 65 organizations in the Asia-Pacific region and 25…
Microsoft has addressed a significant issue affecting users of classic Outlook on devices running Windows 11, version 24H2. After installing…
A cross-site scripting (XSS) vulnerability within the Krpano framework, a popular tool for embedding 360° images and creating virtual tours,…