Category: CyberSecurityNews
ESET’s recent report details the activities of various advanced persistent threat (APT) groups from April to September 2024, highlighting key…
Cybercriminals have launched a large-scale phishing attack using a new variant of Rhadamanthys Stealer, dubbed CopyRh(ight)adamantys, which targets individuals and…
North Korean threat actors, likely associated with BlueNoroff, have launched multi-stage malware attacks targeting cryptocurrency businesses, expanding their toolkit to…
MFA enhances the security of email accounts by requiring users to provide additional verification beyond just their password. Implementing MFA…
Multi-stage malware means sophisticated cyberattack strategies that evolve in several steps. Recent developments in multi-stage malware highlight the increasing sophistication…
Stealer malware is a type of malicious software designed to infiltrate computers and extract sensitive information. Once installed, it communicates…
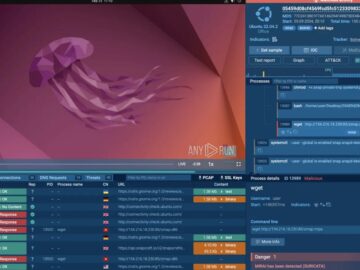
October 2024 has been a productive month for Interactive malware analysis platform ANY.RUN, bringing a series of improvements aimed at…
Hackers primarily target Windows systems due to their significant market share: Over 80% of desktop operating systems run Windows. Not…
Cybercriminals are utilizing a sophisticated evasion strategy called ZIP file concatenation to specifically target Windows users. This method combines several…
Hackers target Cisco primarily due to its critical role in global network infrastructure and security. Cisco’s devices are essential for…
Multiple critical vulnerabilities have been identified in HPE Aruba Access Points, potentially allowing attackers to execute remote code and compromise…
Cisco has disclosed multiple vulnerabilities impacting its Identity Services Engine (ISE) software. These vulnerabilities could allow authenticated, remote attackers to…