Category: CyberSecurityNews
Leeds Equity Partners (“Leeds Equity”) announced today that it has acquired OffSec (the “Company”), the leading provider of continuous cybersecurity…
If you’re managing an SIEM (Security Information and Event Management) system, you know how vital centralized threat detection is. SIEM…
EDRSilencer is a tool designed to enhance data privacy and security by “silencing” or “blocking” unwanted data transmissions from endpoints….
A code signing certificate is a digital certificate that allows software developers to sign their applications. This ensures both the…
In a disturbing development for e-commerce security, cybersecurity experts have revealed that threat actors are actively exploiting the CosmicSting vulnerability…
Volt Typhoon is a Chinese state-sponsored hacking group that has been active since at least mid-2021, targeting critical infrastructure sectors…
Cerberus is an advanced Android banking trojan that emerged in 2019, primarily designed to steal sensitive “financial information.” While this…
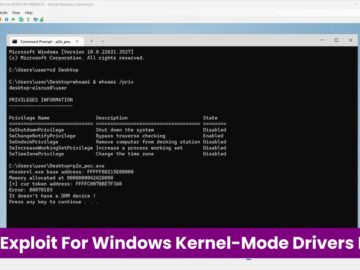
A critical vulnerability in Windows Kernel-Mode Drivers has been exposed with the release of a Proof-of-Concept (PoC) exploit, allowing attackers…
A group of threat actors, led by the notorious hacker known as IntelBroker, has claimed responsibility for a significant data…
A recently identified vulnerability in Ubuntu’s Authd, CVE-2024-9312, has raised significant security concerns. The flaw, present through version 0.3.6, allows…
Researchers have uncovered a sophisticated attack campaign targeting Ivanti Cloud Services Appliance (CSA) users. Nation-state actors are exploiting multiple zero-day…
Jetpack, a popular WordPress plugin, has released a critical security update. Version 13.9.1 was launched earlier today to address a…