Category: CyberSecurityNews
Threat actors target the “PyPI” primarily due to its vast user base and the ease of distributing malicious packages within…
Fraudulent trading apps have emerged as a significant threat to users in cyberspace. As these applications target and lure victims…
Adobe Commerce (formerly known as Magento) is a robust e-commerce platform owned by Adobe that provides flexible and scalable solutions…
Cryptocurrency scammers temporarily compromised the LEGO website to deceive fans into buying a fake “LEGO Coin” cryptocurrency. The breach occurred…
Cyber extortion is a cybercrime under which the threat actors illicitly access “sensitive data” in systems and demand a “ransom”…
The Cybersecurity and Infrastructure Security Agency (CISA) has issued an urgent alert regarding the active exploitation of critical vulnerabilities in…
Visual Studio is a powerful integrated development environment from Microsoft and it’s primarily used for developing apps on the “.NET…
A sophisticated and elusive malware known as “Perfctl,” has been discovered targeting millions of Linux servers worldwide. Researchers at Aqua…
An exclusive live webinar will take place on October 4th at noon Eastern Time (ET), demonstrating how Criminal IP’s Attack…
At DEF CON 32, the SquareX research team delivered a hard-hitting presentation titled Sneaky Extensions: The MV3 Escape Artists where…
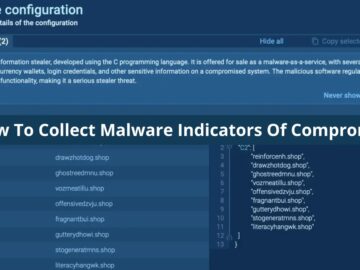
Indicators of Compromise (IOCs) are critical forensic artifacts that cybersecurity researchers use to “detect,” “investigate,” and “mitigate” security threats. As…
Threat actors are increasingly relying on Telegram and Discord apps for data exfiltration. Analysts at ANY.RUN shared a detailed guide…