Category: CyberSecurityNews
In a recent security advisory, Cisco has disclosed multiple vulnerabilities affecting its Small Business RV340, RV340W, RV345, and RV345P Dual…
Cisco has issued a security advisory regarding a critical vulnerability in its Nexus Dashboard Fabric Controller (NDFC). This flaw could…
Montreal-based video game developer Red Barrels, known for its critically acclaimed Outlast series, has recently experienced a significant cybersecurity breach….
Aembit, the non-human IAM company, today announced the appointment of Mario Duarte as chief information security officer (CISO). Duarte, formerly…
Zimbra, a popular email and collaboration platform, has issued a crucial security update to patch a severe vulnerability in its…
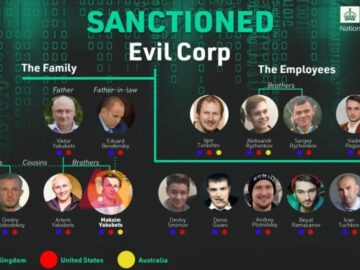
Authorities in the UK, US, and Australia have sanctioned sixteen individuals linked to Evil Corp, a group once considered the…
A recently identified vulnerability in Bluetooth technology, identified as CVE-2020-26558, poses a significant security risk to devices supporting various Bluetooth…
An ongoing fake Google Chrome update effort targeting France has been noticed, which spreads WarmCookie malware via compromised websites. WarmCookie…
The 8220 hacker group is known for targeting both Windows and Linux web servers by deploying “crypto-jacking” malware to exploit…
XWorm refers to a type of malware that has been analyzed for its obfuscation techniques and potential impacts on systems….
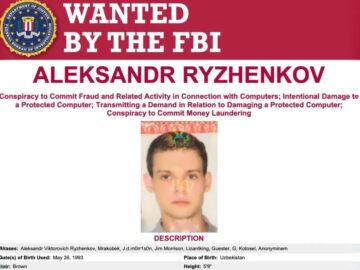
Law enforcement agencies have identified Russian national Aleksandr Viktorovich Ryzhenkov as a key member of the notorious Evil Corp cybercrime…
Docker Swarm and Kubernetes are both container orchestration tools, but they serve different use cases.SSH servers can be utilized alongside…