Category: CyberSecurityNews
Nowadays, organizations face increasing cybersecurity threats that can lead to significant financial and reputational damage. Cybersecurity involves implementing and executing…
A newly discovered vulnerability in Apache Tomcat, identified as CVE-2024-38286, has raised significant concerns among cybersecurity experts. This flaw allows…
GeoServer is an open-source server written in Java that enables users to share, process, and edit geospatial data. It supports…
A critical unauthenticated Remote Code Execution (RCE) vulnerability has been discovered, impacting all GNU/Linux systems. As per agreements with developers,…
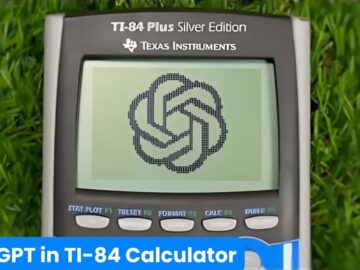
A YouTube creator known as “ChromaLock” has successfully modified a Texas Instruments TI-84 graphing calculator to connect to the internet…
In a surprise move, Kaspersky customers in the United States have discovered that their antivirus software has been automatically replaced…
RansomHub is well-known for its affiliate scheme and for employing methods to turn off or disable endpoint detection and response…
Thousands of WordPress sites have been exposed to potential threats due to vulnerabilities in the Houzez theme and WordPress Houzez…
Quishing, or QR code phishing, is rapidly evolving as threat actors adapt their tactics to bypass email security scanners. By…
Organizations must adopt proactive measures to safeguard their digital assets. One of the most effective strategies involves collaborating with red…
Apache Axis is a web service engine that provides the capability to add web service interfaces to web applications. It…
A hacking forum post has surfaced, claiming that Oracle Corporation, a leading multinational computer technology company, has suffered a data…