Category: CyberSecurityNews
A C2 framework is an architecture that controls and maintains access to compromised systems. Its purpose is to allow you…
Supershell is a command-and-control (C2) remote control platform that operates through web services. It allows users to establish a reverse…
Fox Kitten (aka Pioneer Kitten or Parisite) is an Iranian cyber threat group that has been active since at least…
Phishing attacks are a type of social engineering scam where attackers trick victims into revealing sensitive information. In phishing attacks,…
Managed Services Providers (MSPs) are increasingly looking to provide cybersecurity services based on heightened demand from their current clients. Though…
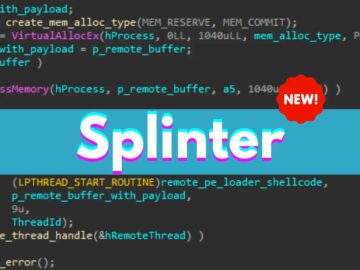
Unit 42 cybersecurity researchers have identified a new post-exploitation red team tool, Splinter, using Advanced WildFire’s memory scanning tools. This…
A botnet is a network of compromised devices, such as computers and IoT devices, infected with malware and controlled by…
A botnet, short for “robot network,” is a collection of internet-connected devices, including computers, servers, mobile devices, and Internet of…
Aembit, the non-human identity and access management (IAM) company, today released its 2024 Non-Human Identity Security Report, a definitive survey…
The Tor Project has responded to recent reports that law enforcement agencies in Germany have successfully infiltrated the Tor network…
The Cybersecurity and Infrastructure Security Agency (CISA) has issued an urgent warning regarding five critical vulnerabilities that are being actively…
Threat actors often make use of weaponized PDF files as they enable them to deliver malware and execute attacks through…