Category: CyberSecurityNews
The Cybersecurity and Infrastructure Security Agency (CISA) has issued an urgent warning regarding five critical vulnerabilities that are being actively…
Threat actors often make use of weaponized PDF files as they enable them to deliver malware and execute attacks through…
In a recent cyberattack, Russian cybersecurity firm Doctor Web (Dr.Web) was forced to disconnect all its servers to mitigate the…
A joint cybersecurity advisory issued by the Federal Bureau of Investigation (FBI), Cyber National Mission Force (CNMF), and National Security…
Research indicates that an infostealer malware infection is often a precursor to a ransomware attack SpyCloud, the leader in Cybercrime…
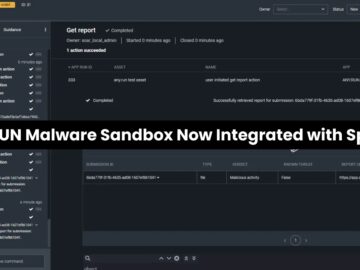
Splunk users can now leverage ANY.RUN’s sandbox and threat intelligence directly within their Splunk SOAR environment. This allows for the…
Law enforcement agencies have successfully dismantled “Ghost,” a sophisticated encrypted communication platform allegedly designed exclusively for criminal use. The operation,…
Block ciphers are a fundamental component of modern cryptography, crucial in securing data across various digital platforms. Unlike stream ciphers,…
Trojanized PDF readers are malicious software that are disguised as legitimate PDF viewing applications. They are primarily used by the…
INE Security is proud to announce that it has been named a winner in the prestigious 2024 SC Awards, named…
Microsoft has issued a critical warning regarding a Windows kernel vulnerability that could lead to the disclosure of sensitive information….
Malvertising (malicious advertising) refers to the practice of embedding harmful code within online advertisements, which can lead to malware infections…