Category: CyberSecurityNews
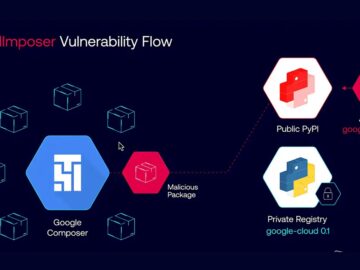
Security researchers revealed this week that a critical remote code execution (RCE) vulnerability in Google Cloud Platform (GCP) could have…
Analysis of millions of real-world NHI secrets by Entro Security Labs reveals widespread, significant risks, emphasizes need for improved Secrets…
The Windows MSHTML platform spoofing vulnerability, CVE-2024-43461, which affects all supported Windows versions, has been exploited in the wild. CVE-2024-43461…
In a significant security alert, millions of D-Link routers are at risk due to critical vulnerabilities that have been discovered…
Recent developments in Android malware have revealed a concerning trend where malicious applications are increasingly capable of stealing banking login…
Remcos is a Remote Access Trojan (RAT) that allows attackers to gain unauthorized control over infected computers. This RAT has…
In cybersecurity, a honeypot is a bait system specifically designed to attract and analyze cyber-attacks, functioning as a trap for…
With the global cost of cybercrime reaching nearly $9.4 million in 2024, organizations are under immense pressure to protect their…
A Twitter account known as DarkWebInformer has claimed that a notorious hacker, identified only by the alias “888,” has allegedly…
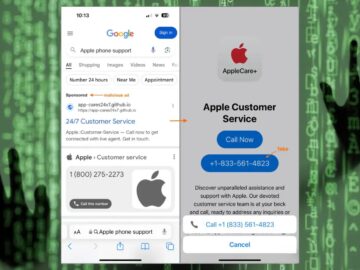
A malicious campaign targeting Mac users seeking support or extended warranty services through AppleCare+ has been uncovered. This scam involves…
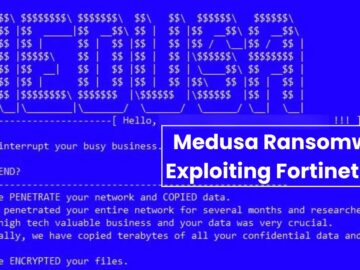
The notorious Medusa ransomware group has been exploiting a critical vulnerability in Fortinet’s FortiClient EMS software to launch sophisticated ransomware…
A critical vulnerability was recently discovered in Azure API Management (APIM) that allowed users with Reader-level access to escalate their…