Category: CyberSecurityNews
The Latrodectus malware has been observed to have enhanced capabilities and sophisticated evasion techniques. Initially discovered by Walmart in October…
Microsoft discovered a North Korean threat actor exploiting a zero-day vulnerability in the Chromium browser, identified as CVE-2024-7971. This vulnerability,…
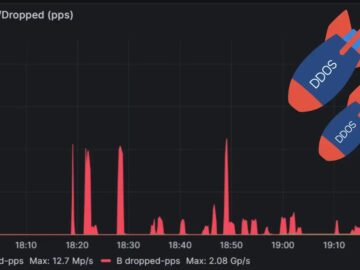
Global Secure Layer (GSL) successfully mitigated the most considerable packet rate of the Distributed Denial of Service (DDoS) attack ever…
A new ransomware group, Cicada3301, has emerged, targeting Windows and Linux/ESXi hosts with sophisticated encryption techniques. First observed in June…
Welcome to this week’s edition of our Weekly Cybersecurity Newsletter, your go-to source for the latest developments and insights in the…
As of August 2024, Iran-based cyber actors continue to exploit U.S. and foreign organizations across multiple sectors. The primary sectors…
Threat actors often target the popular code repository platform “GitHub” due to it’s wide use, and features that this platform…
In the ever-evolving landscape of cybersecurity, malware obfuscation techniques are advancing rapidly. As security measures improve, so do malicious actors’…
Cary, North Carolina, August 30th, 2024, CyberNewsWire: INE Security is pleased to announce that it has been recognized as a…
The events surrounding Pavel Durov’s arrest on 24 August 2024 due to Telegram’s suspected operational crimes worsened discussions on topics…
Researchers discovered that a malicious Chrome extension dubbed “Bull Checker” had been targeting people on multiple Solana-related subreddits. The Jupiter…
In a detailed continuation of the Linux Detection Engineering series, Elastic Security’s Ruben Groenewoud has released an in-depth exploration of…