Category: CyberSecurityNews
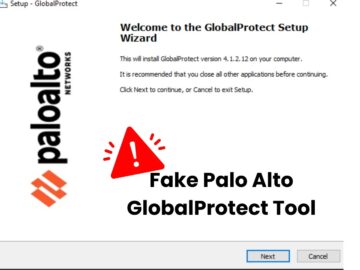
A sophisticated malware targeting organizations in the Middle East is posing a significant threat. Disguised as a legitimate Palo Alto…
Researchers observed a significant surge in phishing attacks targeting MS Office credentials via Microsoft Sway in July 2024, where attackers…
Cisco has disclosed a critical vulnerability in its NX-OS software that could allow unauthenticated, remote attackers to cause a denial…
A botnet is exploiting a new zero-day vulnerability, CVE-2024-7029, in AVTECH CCTV cameras to spread a Mirai variant, which is…
A critical vulnerability in the Dell Client Platform BIOS has been identified, potentially allowing hackers to hijack compromised systems. This…
Check Point® Software Technologies Ltd. (NASDAQ: CHKP), a prominent player in the cybersecurity industry, has announced a definitive agreement to…
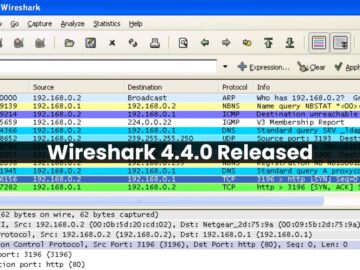
The Wireshark Foundation has announced the release of Wireshark 4.4.0, bringing a host of new features, improvements, and bug fixes…
Artificial intelligence (AI) platforms have become integral tools for businesses and organizations worldwide. These technologies promise efficiency and innovation, from…
Security researchers have discovered that the BlackByte ransomware group is actively exploiting a recently patched authentication bypass vulnerability in VMware…
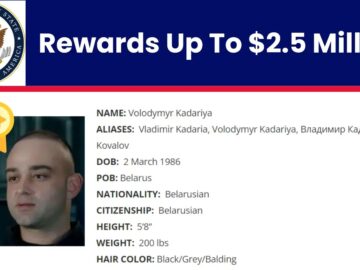
The U.S. Department of State has announced a reward of up to $2.5 million for information leading to Volodymyr Kadariya’s…
ESET researchers have uncovered two critical zero-day vulnerabilities in WPS Office for Windows, exploited by the advanced persistent threat (APT)…
Hackers target macOS as its growing user base makes it an increasingly attractive target. Despite its reputation for strong security,…