Category: CyberSecurityNews
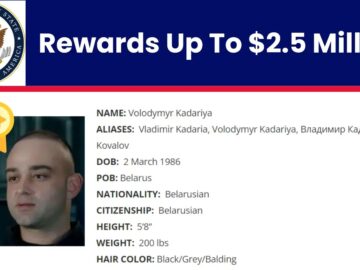
The U.S. Department of State has announced a reward of up to $2.5 million for information leading to Volodymyr Kadariya’s…
ESET researchers have uncovered two critical zero-day vulnerabilities in WPS Office for Windows, exploited by the advanced persistent threat (APT)…
Hackers target macOS as its growing user base makes it an increasingly attractive target. Despite its reputation for strong security,…
The popular learning platform Moodle was found to have a critical vulnerability that allowed for remote code execution, which was…
Researchers have uncovered significant cybersecurity vulnerabilities in the wireless gear-shifting systems of high-end bicycles, particularly those using Shimano’s Di2 technology….
The Cybersecurity and Infrastructure Security Agency (CISA) and the Federal Bureau of Investigation (FBI) have detailed the latest phishing techniques…
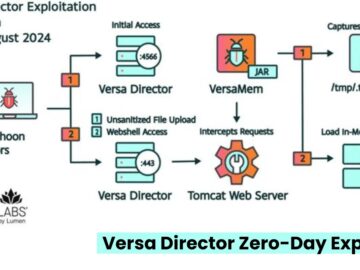
Chinese state-sponsored threat actors have been exploiting a zero-day vulnerability in Versa Director servers, identified as CVE-2024-39717. This vulnerability, discovered…
Fortra has urgently released patches to address two critical SQL injection vulnerabilities in its FileCatalyst Workflow software, identified as CVE-2024-6632…
The eight Android and iOS apps fail to adequately protect user data, which transmits sensitive information, such as device details,…
Cisco has announced its intent to acquire Robust Intelligence, a leader in AI application security. This acquisition aligns with Cisco’s…
Researchers have revealed that a critical security flaw in Microsoft 365 Copilot allowed attackers to exfiltrate sensitive user information through…
Argentine authorities have dismantled a sophisticated cryptocurrency operation based in Buenos Aires. The operation, which was allegedly connected to North…