Category: CyberSecurityNews
The National Cyber Security Centre (NCSC) of Ireland has warned about a growing trend of WhatsApp verification code scams targeting…
The Hillstone WAF is designed to provide enterprise-class security for web servers, applications, and APIs from various cyber threats. It…
Mirai botnets have played a major role in DDoS attacks worldwide specifically against IoT devices and servers. Mirai was discovered…
Hackers often abuse Linux malware since Linux systems are widely used in critical servers and infrastructure for their operation. By…
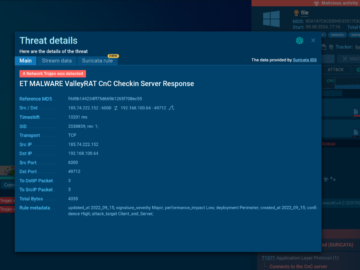
Researchers at ANY.RUN uncovered a sophisticated attack targeting Chinese-speaking users. The attack is spreading multi-stage malware known as ValleyRAT, which is designed…
Deniss Zolotarjovs, 33, from Moscow, Russia, was charged with federal crimes in the U.S. District Court in Cincinnati today. A…
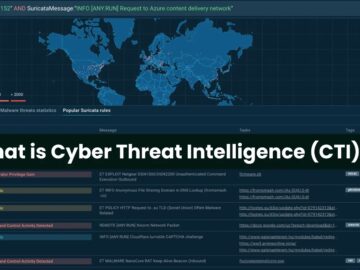
Cyber Threat Intelligence (CTI), also known as Threat Intelligence or Threat Intelligence, is a critical practice in cybersecurity. It involves…
Threat actors successfully deployed BlackSuit ransomware after maintaining access to a compromised network for 15 days. The intrusion, which began…
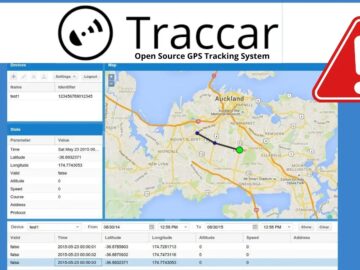
Two critical vulnerabilities have been discovered in the Traccar GPS. These vulnerabilities, CVE-2024-31214 and CVE-2024-24809, allow unauthenticated attackers to execute…
Security researchers have recently identified a new malware strain that employs advanced obfuscation techniques to evade detection by antivirus software….
Researchers uncovered a new type of denial-of-service (DoS) attack, known as the D(HE)at attack, exploits the computational demands of the…
WhatsApp’s security teams have identified and blocked a cluster of malicious activities originating from Iran. The targeted campaign, linked to…