Category: CyberSecurityNews
WhatsApp’s security teams have identified and blocked a cluster of malicious activities originating from Iran. The targeted campaign, linked to…
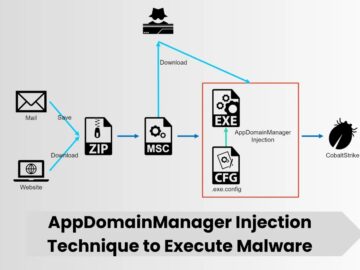
Cybersecurity experts have observed a surge in attacks leveraging a relatively unknown technique known as AppDomainManager Injection to execute malware…
Pavel Durov, Telegram’s 39-year-old billionaire founder and CEO, was arrested on Sunday at Le Bourget Airport near Paris. French authorities…
In the ever-evolving landscape of cybersecurity, the past week has highlighted several critical developments and ongoing challenges faced by organizations…
A new variant of Copybara, an Android malware family, has been detected to be active since November 2023 spreading through…
Cybersecurity analysts at Mandiant recently identified a stealthy memory malware dubbed “PEAKLIGHT.” A Stealth memory malware is often referred to…
Global geopolitical tensions are as bad as they’ve been in a long time. In this context, cyber warfare threatens our…
The National Security Agency (NSA) has released the Best Practices for Event Logging and Threat Detection across cloud services, enterprise…
A critical remote code execution (RCE) vulnerability in Microsoft Edge has been discovered. It could allow attackers to take control…
Dell Technologies has identified a security vulnerability in Dell Power Manager (DPM), affecting versions 3.15.0 and prior. This vulnerability, identified…
Hackers often target and exploit Amazon services due to their vast offerings, including massive computer power, storage, and global reach….
In recent years, the belief that macOS systems are immune to malware has been increasingly challenged. With the emergence of…