Category: CyberSecurityNews
A critical vulnerability identified as CVE-2024-6915 has been discovered in JFrog Artifactory, a widely used repository manager. This flaw, categorized…
A critical zero-day vulnerability in Apache OFBiz, an open-source enterprise resource planning (ERP) system, has been discovered that could allow…
Cybersecurity experts have uncovered a series of attacks targeting organizations in Kazakhstan by a threat actor dubbed “Bloody Wolf.” The…
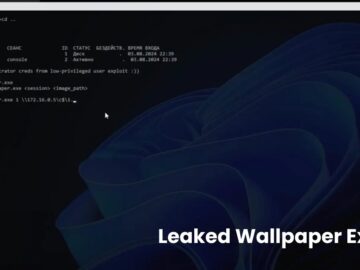
A critical security flaw in Windows’ wallpaper handling mechanism has been uncovered. It allows attackers to gain system-level privileges on…
Cisco Talos has unearthed a sophisticated cyber-espionage campaign targeting a Taiwanese government-affiliated research institute. The attack, attributed to the notorious…
Ransomware operators often acquire malware through purchases on the dark web, group affiliations, and leaked source codes rather than developing…
Cybersecurity researcher Jeremiah Fowler discovered and reported to VpnMentor about 13 non-password-protected databases containing 4.6 million documents, including sensitive voter…
The communication between DNS recursive resolvers and authoritative nameservers is largely unsecured, making it susceptible to on-path and off-path attacks….
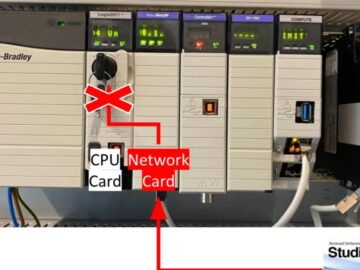
A critical security vulnerability in Rockwell Automation’s ControlLogix and GuardLogix controllers has been discovered. This vulnerability could potentially allow attackers…
Multiple digital Video Recorder (DVR) devices have been identified with a critical security vulnerability, leaving over 408,000 units exposed to potential cyber-attacks….
Security researchers have discovered a new way that hackers can steal sensitive information, like passwords. This involves eavesdropping on HDMI…
Stay up to date with cybersecurity news! Our Weekly Cybersecurity Newsletter provides a curated summary of the most important updates,…