Category: CyberSecurityNews
Progress Software has disclosed a new high-severity vulnerability in its MOVEit Transfer file transfer solution that could allow attackers to…
Maintaining continuous vigilance is essential for organizations of all sizes in the face of increasing cyber threats. However, lean IT…
A grand jury in Kansas City has charged North Korean national Rim Jong Hyok for orchestrating a series of cyberattacks…
HealthEquity, Inc., a prominent health savings account administrator, has reported a data breach affecting approximately 4.3 million individuals. The breach,…
DigiCert, a major certificate authority, to revoke thousands of SSL/TLS certificates because of a Domain Control Verification error. This could…
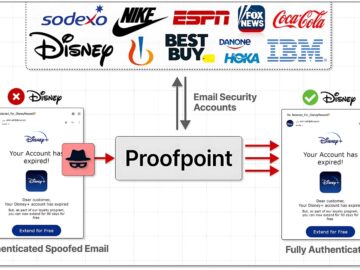
A massive phishing campaign dubbed “EchoSpoofing” has exploited a critical vulnerability in Proofpoint’s email protection service, allowing cybercriminals to send…
Microsoft researchers have found a critical vulnerability in VMware’s ESXi hypervisors. Ransomware operators are using this problem to attack systems….
As Americans engage in major activities such as the 2024 presidential race, large-scale cultural festivals, and high-profile sporting events, cybersecurity…
Due to their widespread use, popular productivity tools are often targeted and attacked by hackers. These tools create a large…
Researchers identified a new attack campaign (“Operation ShadowCat”) using malicious LNK files distributed via spam emails, which triggers a PowerShell…
By exploiting OS command injection vulnerabilities, threat actors can run arbitrary commands on a host operating system to obtain unauthorized…
Void Banshee, a threat actor, has been exploiting a critical MSHTML vulnerability, CVE-2024-38112, to distribute the Atlantida InfoStealer malware. This…