Category: CyberSecurityNews
The LI.FI Protocol, a cross-chain bridging and swapping platform, was the victim of a sophisticated cyber-attack that stole approximately $9.7…
Managed Services Providers (MSPs) are increasingly looking to provide cybersecurity services due to the demand from their current clients. Though…
Cybersecurity researchers discovered one of the largest data breaches in history, with 361 million unique emails, usernames, and passwords now…
BMW Hong Kong has reportedly suffered a data breach affecting approximately 14,000 customers. The leak, which came to light on…
Attackers are actively exploiting a critical remote code execution (RCE) vulnerability in Apache HugeGraph-Server, which is tracked as CVE-2024-27348. The…
NETGEAR has released an update to the firmware to address a high-severity authentication bypass vulnerability that currently affects CAX30 models. …
The FBI revealed on Monday that they have achieved access to the phone of the alleged shooter, Thomas Matthew Crooks,…
Hackers target legitimate Remote Monitoring and Management (RMM) tools as they provide powerful, trusted access to systems and networks. This…
A critical vulnerability has been discovered in the popular Profile Builder and Profile Builder Pro plugins, with over 50,000 active…
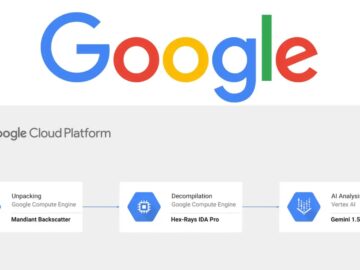
The ability to swiftly and accurately analyze malware is paramount. Traditional reverse engineering and code analysis methods are often too…
The Cybersecurity and Infrastructure Security Agency (CISA) has issued an urgent alert regarding a critical Remote Code Execution (RCE) vulnerability…
Pinterest, the popular image-sharing platform with over 518 million monthly active users, faces a potential data leak that could affect…