Category: CyberSecurityNews
A critical use-after-free vulnerability has been discovered in the Linux kernel’s netfilter subsystem. This vulnerability could potentially allow local, unprivileged…
Cybersecurity researchers uncovered a sophisticated attack campaign by the Water Sigbin (aka 8220 Gang) threat actor that exploited vulnerabilities in…
Google has announced that its Chrome browser will stop trusting TLS server authentication certificates issued by Entrust and AffirmTrust starting…
Transitioning to SAP Cloud offers many advantages—from improved performance to easier data models—but it also increases a couple of inherent…
Hackers target and abuse npm packages to inject malicious code into widely used software libraries, reaching many developers and applications….
JTBC, a prominent Korean news organization, has uncovered that KT Corporation, one of South Korea’s largest telecom providers, deliberately infected…
Hackers abuse Chrome extensions since they can embed malware on many targets by using common extensions in the browser. These…
Juniper Networks has disclosed a critical vulnerability (CVE-2024-2973) affecting its Session Smart Router (SSR) and Session Smart Conductor products. The…
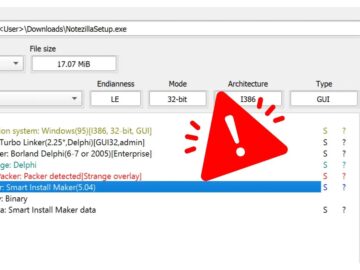
Cybersecurity firm Rapid7 has identified that popular Windows tools Notezilla, RecentX, and Copywhiz have been weaponized to deliver malware. These…
On Wednesday, June 26, 2024, TeamViewer, a leading provider of remote access software, announced that attackers had compromised its internal…
Infinidat, a leading provider of enterprise storage solutions, has introduced a new automated cyber resiliency and recovery solution that will…
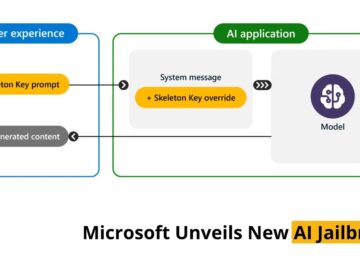
Hackers frequently look for new ways to bypass the ethical and safety measures incorporated into AI systems. This gives them…