Category: CyberSecurityNews
A critical vulnerability has been discovered in several models of ASUS routers. It allows unauthenticated remote attackers to execute arbitrary…
Our weekly summary of cybersecurity news provides information on the most recent threats, vulnerabilities, innovations, attacks, dangers, and stories in…
Threat actors abuse high-performance bots to carry out large-scale automated attacks efficiently. These bots can work quickly, flood systems, steal…
Linux systems are deployed mostly in servers, in the cloud, and in environments that are considered vital; consequently, they are…
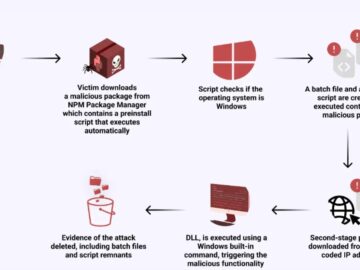
In December 2023, we reported on how North Korean threat actors, particularly Jade Sleet, have been compromising supply chains through…
Life360, a company known for its family safety services, recently fell victim to a criminal extortion attempt. The company received…
Microsoft has announced that it will delay the broad release of its AI-powered Recall feature for Windows Copilot+ PCs, following…
Hackers misuse malware for diverse illicit intentions, including data theft, disrupting systems, espionage, or distortion for unethical monetary benefits. Besides…
Hackers use Windows Search’s vulnerability to penetrate different layers and rooms in the client’s systems and execute unauthorized code by…
GitHub, the world’s leading software development platform, is celebrating a milestone: the 10th anniversary of its Security Bug Bounty program….
Kulicke and Soffa Industries, Inc. (K&S), a leading semiconductor packaging and electronic assembly solutions provider, has disclosed a data breach…
A threat actor has claimed responsibility for breaching Israel’s government API database. The announcement was made via a post on…