Category: CyberSecurityNews
A Russian citizen has been indicted for working as an “access broker” and selling unauthorized access to computer networks, including…
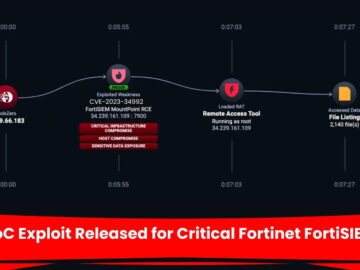
A proof-of-concept (PoC) exploit has been released for a critical vulnerability in Fortinet’s FortiSIEM. The vulnerability, CVE-2024-23108, allows for remote,…
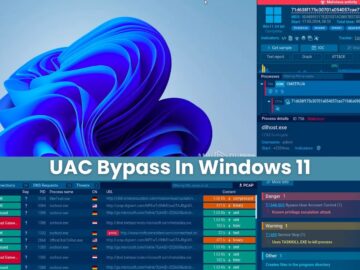
User Account Control (UAC) is one of the security measures introduced by Microsoft to prevent malicious software from executing without…
A critical vulnerability was found in the Replicate AI platform that could have exposed the private AI models and application…
Hackers often target routers as the gateways that connect devices and networks to the internet. Besides this, they are lucrative…
Managed service providers (MSPs) are on the front lines of soaring demand for cybersecurity services as cyberattacks increase in volume…
A stalkerware company with poor security practices is exposing victims’ data as the software, designed for unauthorized device monitoring, leaked…
Security experts have disclosed advanced methods for bypassing Web Application Firewalls (WAFs) on a large scale, and they have also…
A new privilege escalation vulnerability has been discovered in Zscaler Client Connector, combining three different vulnerabilities. The three vulnerabilities were…
Sav-Rx, a healthcare company based in Fremont, Nebraska, has disclosed a major data breach affecting over 2.8 million individuals, including…
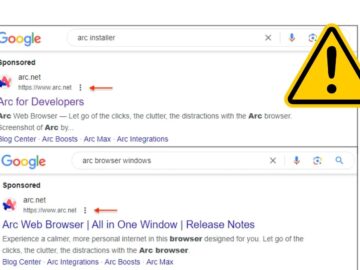
Google Chrome has been the dominant web browser for years now, which is why it may come as a surprise…
It has been reported that a well-known threat actor named “888” has purportedly exposed a database linked to the well-liked…