Category: CyberSecurityNews
The communication between DNS recursive resolvers and authoritative nameservers is largely unsecured, making it susceptible to on-path and off-path attacks….
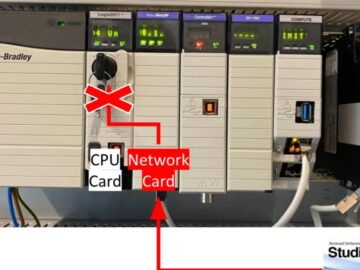
A critical security vulnerability in Rockwell Automation’s ControlLogix and GuardLogix controllers has been discovered. This vulnerability could potentially allow attackers…
Multiple digital Video Recorder (DVR) devices have been identified with a critical security vulnerability, leaving over 408,000 units exposed to potential cyber-attacks….
Security researchers have discovered a new way that hackers can steal sensitive information, like passwords. This involves eavesdropping on HDMI…
Stay up to date with cybersecurity news! Our Weekly Cybersecurity Newsletter provides a curated summary of the most important updates,…
TgRat, a Telegram-controlled trojan, was discovered attacking Linux servers in an attempt to steal data from a compromised system. In…
Threat actors have been exploiting the attack vector known as Sitting Ducks since at least 2019 to conduct malware delivery,…
Security researchers have discovered a severe vulnerability in the Linux kernel that could allow attackers to gain full control over…
In mid-2022, Mandiant’s Managed Defense first uncovered UNC4393, the primary user of BASTA ransomware. This financially motivated threat cluster has…
A Russian threat actor known as Fighting Ursa (also referred to as APT28, Fancy Bear, and Sofacy) has been identified…
Researchers from ANY RUN identified a malware distribution campaign dubbed DeerStealer that leverages deceptive websites masquerading as legitimate Google Authenticator…
A sophisticated phishing campaign targets Microsoft OneDrive users, employing social engineering to trick victims into executing malicious PowerShell scripts. The…