Category: CyberSecurityNews
A proof of Concept (PoC) has been published for a critical Remote Code Execution (RCE) vulnerability identified in Fortra’s FileCatalyst…
New research has revealed that more than 900 websites had a serious misconfiguration, which exposed a massive 125 million user…
The National Cyber Security Centre (NCSC) of the United Kingdom has recently published a comprehensive set of guidelines designed to…
Cisco has officially completed its acquisition of Splunk for a staggering $28 billion. This strategic acquisition marks a milestone in…
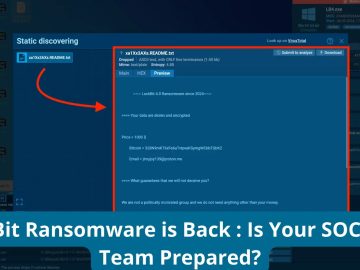
Law enforcement disrupted LockBit ransomware operations in February, seizing infrastructure and their website. Regretfully, the victory appears to have been…
A new Advanced Persistent Threat (APT) campaign, dubbed Earth Krahang, has emerged with a focus on infiltrating government entities across…
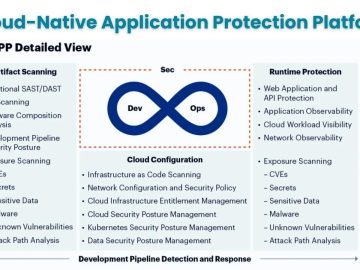
Multi-cloud and hybrid infrastructures are becoming the norm among enterprises nowadays. Around 9 in 10 companies use a multi-cloud strategy,…
A vulnerability classified as improper input validation was found in Zoom Desktop Client for Windows, Zoom VDI Client for Windows,…
A new threat looms over Android users, masquerading as a routine Chrome update. This deceptive tactic breaches trust and directly…
Researchers at Hadess have identified a critical vulnerability in the widely-used Korenix JetlO industrial Ethernet switch series. The flaw tracked…
Fujitsu has announced the discovery of malware on several of its business computers, raising concerns over the potential leak of…
A new malware campaign has been identified targeting Android users in India. This sophisticated attack distributes malicious APK packages to…