Category: CyberSecurityNews
OPNsense has released an update focused on eliminating security vulnerabilities and improving firewall performance. The latest version includes third-party security…
A critical vulnerability in Cisco Identity Services Engine (ISE) could allow remote attackers to crash the system through a crafted…
NVIDIA has patched a critical vulnerability in its App for Windows that could allow local attackers to execute arbitrary code…
The Gootloader malware campaign has resurfaced with sophisticated evasion techniques that allow it to bypass automated security analysis. This persistent…
The Russia-aligned Sandworm threat group has intensified its destructive cyberattacks against Ukrainian organizations, deploying sophisticated data wiper malware designed to…
The emergence of advanced AI browsing platforms such as OpenAI’s Atlas and Perplexity’s Comet has created a sophisticated challenge for…
The cybersecurity landscape continues to evolve as new ransomware variants emerge from the remnants of previous campaigns. Midnight ransomware represents…
A previously unidentified Iranian threat actor has emerged with sophisticated social engineering tactics aimed at academics and foreign policy experts…
ValleyRAT has emerged as a sophisticated multi-stage remote access trojan targeting Windows systems, with particular focus on Chinese-language users and…
North Korean threat actors are evolving their attack strategies by leveraging developer-focused tools as infection vectors. Recent security discoveries reveal…
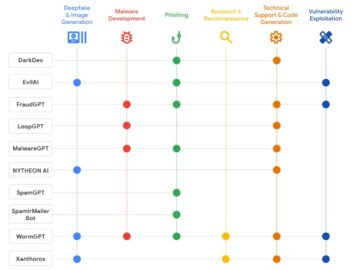
The cybercrime landscape has undergone a dramatic transformation in 2025, with artificial intelligence emerging as a cornerstone technology for malicious…
Security researchers have uncovered a sophisticated new malware family targeting enterprise environments through a supply chain compromise. The malware, tracked…